Nothing you do with a computer will ever be as important as making a solid backup. Hard drives crash, and when yours does, unless you have a backup, you'll find yourself facing expensive data recovery services or worse: lost data.
Now that Windows 7 has been released, many Windows users will be looking to back up their documents and media before upgrading -- an absolutely critical step. Luckily, Windows users have many options, including a very nice built-in back up program that ships with both Windows XP and Vista. Regrettably, the program is somewhat buried, so many users aren't familiar with it.
Depending on your needs, the built-in option may be sufficient. If you'd like an option with some bells and whistles not found in Microsoft's program, numerous third-party apps have got you covered.
There are a number of serious challenges when transferring backups between old and new operating systems. Many backup solutions aren't yet avaiable on Windows 7, or don't work on Windows 7 (e.g. NTBACKUP.EXE), or don't work on Windows 7 and never will be (e.g. Live One Care). There are also complications with correct placement of user settings and user data on a Windows 7 system. Many standard directories have moved, or work differently, and many settings need special treatment when transferring.
Microsoft's Windows Easy Transfer utility provides a one-stop solution.
The Windows Easy Transfer utility provides a number of ways to transfer data from an old computer to a new computer; but it works equally well for transferring data from an old Windows operating system to a freshly installed version of Windows 7. Microsoft specifically recommends this path when upgrading from Windows XP to Windows 7; but it also works when upgrading from Windows Vista 32-bit, to Windows 7 64-bit, or when upgrading to a clean install of Windows 7. Even if you are rolling the dice and performing an in-place Vista-32 to Windows 7-32 upgrade (which actually does work), you may want to consider using Windows Easy Transfer in order to provide a temporary backup of your user data.
Windows Easy Transfer allows you to back up all user files and settings for all users on the computer to an external or network drive. Once you have installed a clean copy of the operating system, you can restore user files and settings to the freshly installed operating system.
Versions of Windows Easy Transfer are available for download for 32-bit XP, 64-bit XP, and for32-bit and 64-bit Vista.
Download and run Windows Easy Tranfer for your platform. When prompted, select "An external hard drive or USB Flash Drive" as the method for transferring data from the old operating system to the new operating system. Later on in the UI sequence you will be asked where you want to store the resulting Easy Transfer file. Despite the title of the option, you can place the file on a secondary internal drive if you want. Just make sure you don't reformat the secondary drive, and lose the transfer file, while installing your shiny new copy of Windows 7.
It's not at all obvious what Windows Easy Transfer does transfer; but my experience has been that it tranfers pretty much everything except files in the Program Files and c:\windows directories. The very last item in the scan report is "Shared Items". And included in the "Shared Items" category are all files and folders that are not otherwise included in user profile directories. You can click on the Shared Item's "Customize" link and then the "Advanced" link to see the list of all files and folders that will be backed up for transfer. By default, pretty much everything was selected or backup on my system, including a few things that I could have done without, such as my "Recorded TV", c:\cygwin, and complete copies of a number of errant programs that had installed themselves outside of the c:\program files, and e:\program files directory.
There are also a number of quirks that I encountered that I would rather have known about before I ran it. When bringing up your clean copy of Windows 7, you need to create an account with the same name as the account you used to create the backup. If the account is different, then all user profile settings for the old account will be restored to the account you are currently using, renaming the account in the process. All other accounts in the backup are created and restored with correct names. Also, if you have multiple disks in the backup, but don't have matching drives when restoring, all folders will be merged onto the single disk when restoring. If there are folders with the same name on both drives on the source system, then they will be merged into the same folder when restoring. In my case, that's pretty much what I wanted, but I have no idea what would happen if there were collisions between data files.
The very nice thing about the Windows Easy Transfer process is that it provides a complete temporary backup while upgrading. If the upgrade fails, you can always restore your transfer to a fresh copy of XP, and be back where you started.
You can also selective restore files, in multiple passes when restoring the easy transfer. My complete recorded TV files for all of Battlestar Gallactica season 4, for example, took 14 hours to back up, when creating the inital transfer. When restoring, I was able to deselect these files, reducing the restore time to a bit over 1 1/2 hours. Now that the DVD set is out, I probably never will restore them, honestly.
Now that you have safely transferred your data, you can turn your attention to simpler challenges, such as reinstalling all your software (which doesn't get backed up by Easy Transfer by default); and finding a new backup program that actually works on Windows 7.
Tuesday, December 15, 2009
Sunday, December 13, 2009
Become a PowerPoint Power User
Microsoft PowerPoint has revolutionized the education process for corporations, conferences and educational establishments everywhere. So if you want to wow the participants in your next meeting, you might want to get to know PowerPoint like a power user.
These advanced tips and tricks will enable you to make your PowerPoint presentation even more powerful.
Setting the Default Text Style
To change the style of the text that appears when you type things that aren't the title or the slide body, do the following: Choose the first layout option and click in the title box. From the Format menu, select Font. Make all the changes that you want there, and then check default for new objects. Next click OK. From that point on, new text will be created in that font style and size.
Changing a Design Template
To change the design template for the title or slide body objects, on the menu select View…Title or Slide Master. Click the body of the slide then right click the slide and choose Group…Ungroup. Delete any part of the design you desire. Then right click and choose Group…Regroup. When completed choose the slide sorter view mode from the lower left-corner of the screen.
Using More Than One Guide
If you like using guides, but wish there were more, you can create additional Guides by simply holding down the CTRL key while dragging on an existing Guide. This will create a new guide. To get rid of guides, just drag them off the edge of the slide.
Creating Pages With Slides and Descriptive Text
If you want to create printable pages that have notes or descriptive text associated each slide, PowerPoint has a feature designed to do just this called Notes Pages, or Speaker's Notes (depending on which version you're using). To view the Notes page for any slide, go to the View menu and select Notes Pages. You will see an image of your slide there, and a placeholder for adding your script, notes, or any other text you wish. You can cut-and-paste text from Word here if you like. To print these pages, bring up the Print dialog, and at the bottom of the dialog where it says "Print What:", select Notes Pages. These pages were originally designed to be used as audience hand outs. To return to the normal view click the Slide View button in the lower right corner.
Building Presentations for Distribution to Others
When making a PowerPoint presentation that will be distributed to other people, there are some important things to watch out for that will cause problems:
1. Stick with the fonts that come installed with Windows; Fancy fonts that appear on your machine will cause problems if everyone else doesn't have them.
2. Avoid embedding sounds and videos: These will not go from Mac to Windows gracefully, and you have to be very careful about how you insert the files in order to get them to "travel" properly. See the FAQ section for more information on this.
3. Design the presentation on the lowest version that you think might be in use. For example, if you want the presentation to be able to be viewed by Mac users (who may not have upgraded to the latest version), you will want to design your presentation in PowerPoint 4.0. If you don't have PowerPoint 4, then you'll want to save your presentation in the lowest format you think people will have. For cross-platform distribution, 4.0 is still your safest bet; for Windows-only distribution, save to PowerPoint 95. When you down-rev save, be prepared for some visual changes in your file -- the previous version may not support some of the features you've put in, so be sure to sanity check your file on several different machines and versions BEFORE you distribute it!
Easily Changing From Caps to Lowercase (or Vice Versa)
If you have text that is in the wrong case, select the text, and then click Shift+F3 until it changes to the case style that you like. Clicking Shift+F3 toggles the text case between ALL CAPS, lowercase, and Initial Capital styles. This useful trick works with Word too!
Nudging Objects
You can use the arrow keys to move objects very small distances. This is a big win for those laptop users who no longer have mice. Select the object, then use your arrow keys. Each press of the key will move the object on "grid unit" (1/12th of an inch, don't ask why); if you hold down the Ctrl key while nudging, or if you have the grid turned off, you can move the objects one pixel at a time.
Saving Across Multiple Diskettes
Since PowerPoint 7.0 (the one in Office 95, also known as PowerPoint '95) you have the option to save large files over multiple diskettes. From the File menu, select Pack and Go. This wizard will compress your PowerPoint presentation and copy the file onto as many floppies as are necessary. (Of course, who uses floppies in 2009? Most computers you'd want to send a presentation to don't even have floppy drives. Burn a CD or DVD, put it on a USB stick, e-mail it, put it on a Web site for others to download ...)
Draw a Line Perfectly Horizontal or Vertical
Depress the Shift key while dragging to create your line.
Draw a Perfect Square
Depress the Shift key while dragging to create your square.
Draw a Perfect Circle
Depress the Shift key while dragging to create your circle.
Quickly Access the Slide Master
Click on the Slide View icon (at the top-left of the screen), while depressing the Shift key.
Create a New Design Template
Click on the File drop down menu, select New and then select the Design Template tab. Select an existing design template that most closely matches what you wish to achieve. Make changes to the slide master as required. Then save the file as a template using the SaveAs command to save the file as a dot file.
Preview a Presentation in Black and White
Click on View > Black and White.
Send to the Back or Bring Forward an Object
Right click on the object, select order, and choose the desired command.
Insert the Copyright Symbol
To insert the copyright © symbol, enter (c) To insert the Trademark ™ symbol enter (tm) To insert the registered ® symbol enter (r). These options are controlled by AutoCorrect (exact location depends on your version of PowerPoint; it's in the Tools menu if you have one). You can turn them off, change them, or add others. For example, you may want to turn off the automatic conversion of (c) to © if you frequently use (a), (b), (c) and so on in your presentation. You can always create symbols another way anyhow.
Saving Shows
Save your presentation as a ‘PowerPoint Show’ (.pps) and your presentation will open straight into screenshow mode. To change a .pps back to a presentation for editing, locate the file name, right click the file name, choose rename, and change the .pps extension to .ppt. A warning about instability will appear, but no harm will be done to the presentation.
Jumping to Screens
In show mode type a number then hit ‘enter’ to go to straight to that screen (i.e., ’1’ to go back to the 1st screen). This is particularly useful if you have a large show for multiple speakers -- just make a note of the slide number where each one starts -- and during rehearsal, simply keying the number and pressing enter, jumps you straight to the right place. It's quick and efficient.
Hiding Screens
In the show mode you can hide your first (or any other) screen until you are ready to start by pressing ‘B’’ to blackout the screen or (‘W’ to ‘whiteout’ the screen) then press the ‘B’ or ‘W’ again to reveal the screen when you are ready.
To Go to the First Slide or Last Slide
Ctrl+Home will take you to the first slide in a presentation, Ctrl+End will take you to the last slide.
Toolbar Tips
You can customize your toolbar to contain buttons for tasks that you routinely conduct. Click View…Toolbars…Customize. Click the Commands Tab and choose the desired task. Click and drag the accompanying icon to your preferred location in the toolbar. Close the customize window.
Setting Up the Show
To set up the presentation to run continuously, click Slide Show…Set Up Show. Check ‘loop continuously until ESC’ and click OK.
To set up the presentation with timed settings on each slide, click Slide Show…Rehearse Timings. As each slide appears a rehearsal clock will appear in the upper left corner. When the desired time has expired click the mouse to progress to the next slide. After viewing the entire show you will be asked if you wish to save the rehearsed time. Click Yes.
To record your own narration for the presentation click Slide Show…Record Narration.
Printing the Presentation
You have many options for printing your presentation. Click File…Print. You can choose to print it as slides or handouts and choose how many will fit on a page, print it as a Notes Page, or print it in the outline view. Other options include to print it in Grayscale, Pure Black and White, or with Animations. You can also choose to print only specific slide numbers or print all slides.
Scrolling Credits
Scrolling text can be an effective means of ending or beginning a presentation. Click the desired text. When the Custom Animation text box opens, click the Effects tab. Click the arrow at the right side of the Entry Animation list box to expand the list. Locate Crawl From Bottom and select it. Check the list box labeled Introduce Text. If it isn't set to All at Once, click the arrow at the right side of the list box and select All at Once. Click the Timing tab and select the radio buttons labeled Animate and Automatically. Click OK to close the dialog box and save your changes.
Keyboard Shortcuts Cheat Sheet
* Insert a new slide - CTRL+
* Switch to the next pane (clockwise) - F6
* Switch to the previous pane (counterclockwise) - SHIFT+F6
* Make a duplicate of the current slide - CTRL+D
* Start a slide show - F5
* Promote a paragraph - ALT+SHIFT+LEFT ARROW
* Demote a paragraph - ALT+SHIFT+RIGHT ARROW
* Apply subscript formatting - CTRL+EQUAL SIGN (=)
* Apply superscript formatting - CTRL+PLUS SIGN (+)
* Open the Font dialog box - CTRL+T
* Repeat your last action - F4 or CTRL+Y
* Find - CTRL+F
* View guides - CTRL+G
* Delete a word - CTRL+BACKSPACE
* Capitalize - SHIFT+F3
* Bold - CTRL+B
* Italicize - CTRL+I
* Insert a hyperlink - CTRL+K
* Select all - CTRL+A
* Copy - CTRL+C
* Paste - CTRL+V
* Undo - CTRL+Z
* Save - CTRL+S
* Print - CTRL+P
* Open - CTRL+O
It should be noted that the majority of these shortcuts work in every Office application, not just PowerPoint.
These advanced tips and tricks will enable you to make your PowerPoint presentation even more powerful.
Setting the Default Text Style
To change the style of the text that appears when you type things that aren't the title or the slide body, do the following: Choose the first layout option and click in the title box. From the Format menu, select Font. Make all the changes that you want there, and then check default for new objects. Next click OK. From that point on, new text will be created in that font style and size.
Changing a Design Template
To change the design template for the title or slide body objects, on the menu select View…Title or Slide Master. Click the body of the slide then right click the slide and choose Group…Ungroup. Delete any part of the design you desire. Then right click and choose Group…Regroup. When completed choose the slide sorter view mode from the lower left-corner of the screen.
Using More Than One Guide
If you like using guides, but wish there were more, you can create additional Guides by simply holding down the CTRL key while dragging on an existing Guide. This will create a new guide. To get rid of guides, just drag them off the edge of the slide.
Creating Pages With Slides and Descriptive Text
If you want to create printable pages that have notes or descriptive text associated each slide, PowerPoint has a feature designed to do just this called Notes Pages, or Speaker's Notes (depending on which version you're using). To view the Notes page for any slide, go to the View menu and select Notes Pages. You will see an image of your slide there, and a placeholder for adding your script, notes, or any other text you wish. You can cut-and-paste text from Word here if you like. To print these pages, bring up the Print dialog, and at the bottom of the dialog where it says "Print What:", select Notes Pages. These pages were originally designed to be used as audience hand outs. To return to the normal view click the Slide View button in the lower right corner.
Building Presentations for Distribution to Others
When making a PowerPoint presentation that will be distributed to other people, there are some important things to watch out for that will cause problems:
1. Stick with the fonts that come installed with Windows; Fancy fonts that appear on your machine will cause problems if everyone else doesn't have them.
2. Avoid embedding sounds and videos: These will not go from Mac to Windows gracefully, and you have to be very careful about how you insert the files in order to get them to "travel" properly. See the FAQ section for more information on this.
3. Design the presentation on the lowest version that you think might be in use. For example, if you want the presentation to be able to be viewed by Mac users (who may not have upgraded to the latest version), you will want to design your presentation in PowerPoint 4.0. If you don't have PowerPoint 4, then you'll want to save your presentation in the lowest format you think people will have. For cross-platform distribution, 4.0 is still your safest bet; for Windows-only distribution, save to PowerPoint 95. When you down-rev save, be prepared for some visual changes in your file -- the previous version may not support some of the features you've put in, so be sure to sanity check your file on several different machines and versions BEFORE you distribute it!
Easily Changing From Caps to Lowercase (or Vice Versa)
If you have text that is in the wrong case, select the text, and then click Shift+F3 until it changes to the case style that you like. Clicking Shift+F3 toggles the text case between ALL CAPS, lowercase, and Initial Capital styles. This useful trick works with Word too!
Nudging Objects
You can use the arrow keys to move objects very small distances. This is a big win for those laptop users who no longer have mice. Select the object, then use your arrow keys. Each press of the key will move the object on "grid unit" (1/12th of an inch, don't ask why); if you hold down the Ctrl key while nudging, or if you have the grid turned off, you can move the objects one pixel at a time.
Saving Across Multiple Diskettes
Since PowerPoint 7.0 (the one in Office 95, also known as PowerPoint '95) you have the option to save large files over multiple diskettes. From the File menu, select Pack and Go. This wizard will compress your PowerPoint presentation and copy the file onto as many floppies as are necessary. (Of course, who uses floppies in 2009? Most computers you'd want to send a presentation to don't even have floppy drives. Burn a CD or DVD, put it on a USB stick, e-mail it, put it on a Web site for others to download ...)
Draw a Line Perfectly Horizontal or Vertical
Depress the Shift key while dragging to create your line.
Draw a Perfect Square
Depress the Shift key while dragging to create your square.
Draw a Perfect Circle
Depress the Shift key while dragging to create your circle.
Quickly Access the Slide Master
Click on the Slide View icon (at the top-left of the screen), while depressing the Shift key.
Create a New Design Template
Click on the File drop down menu, select New and then select the Design Template tab. Select an existing design template that most closely matches what you wish to achieve. Make changes to the slide master as required. Then save the file as a template using the SaveAs command to save the file as a dot file.
Preview a Presentation in Black and White
Click on View > Black and White.
Send to the Back or Bring Forward an Object
Right click on the object, select order, and choose the desired command.
Insert the Copyright Symbol
To insert the copyright © symbol, enter (c) To insert the Trademark ™ symbol enter (tm) To insert the registered ® symbol enter (r). These options are controlled by AutoCorrect (exact location depends on your version of PowerPoint; it's in the Tools menu if you have one). You can turn them off, change them, or add others. For example, you may want to turn off the automatic conversion of (c) to © if you frequently use (a), (b), (c) and so on in your presentation. You can always create symbols another way anyhow.
Saving Shows
Save your presentation as a ‘PowerPoint Show’ (.pps) and your presentation will open straight into screenshow mode. To change a .pps back to a presentation for editing, locate the file name, right click the file name, choose rename, and change the .pps extension to .ppt. A warning about instability will appear, but no harm will be done to the presentation.
Jumping to Screens
In show mode type a number then hit ‘enter’ to go to straight to that screen (i.e., ’1’ to go back to the 1st screen). This is particularly useful if you have a large show for multiple speakers -- just make a note of the slide number where each one starts -- and during rehearsal, simply keying the number and pressing enter, jumps you straight to the right place. It's quick and efficient.
Hiding Screens
In the show mode you can hide your first (or any other) screen until you are ready to start by pressing ‘B’’ to blackout the screen or (‘W’ to ‘whiteout’ the screen) then press the ‘B’ or ‘W’ again to reveal the screen when you are ready.
To Go to the First Slide or Last Slide
Ctrl+Home will take you to the first slide in a presentation, Ctrl+End will take you to the last slide.
Toolbar Tips
You can customize your toolbar to contain buttons for tasks that you routinely conduct. Click View…Toolbars…Customize. Click the Commands Tab and choose the desired task. Click and drag the accompanying icon to your preferred location in the toolbar. Close the customize window.
Setting Up the Show
To set up the presentation to run continuously, click Slide Show…Set Up Show. Check ‘loop continuously until ESC’ and click OK.
To set up the presentation with timed settings on each slide, click Slide Show…Rehearse Timings. As each slide appears a rehearsal clock will appear in the upper left corner. When the desired time has expired click the mouse to progress to the next slide. After viewing the entire show you will be asked if you wish to save the rehearsed time. Click Yes.
To record your own narration for the presentation click Slide Show…Record Narration.
Printing the Presentation
You have many options for printing your presentation. Click File…Print. You can choose to print it as slides or handouts and choose how many will fit on a page, print it as a Notes Page, or print it in the outline view. Other options include to print it in Grayscale, Pure Black and White, or with Animations. You can also choose to print only specific slide numbers or print all slides.
Scrolling Credits
Scrolling text can be an effective means of ending or beginning a presentation. Click the desired text. When the Custom Animation text box opens, click the Effects tab. Click the arrow at the right side of the Entry Animation list box to expand the list. Locate Crawl From Bottom and select it. Check the list box labeled Introduce Text. If it isn't set to All at Once, click the arrow at the right side of the list box and select All at Once. Click the Timing tab and select the radio buttons labeled Animate and Automatically. Click OK to close the dialog box and save your changes.
Keyboard Shortcuts Cheat Sheet
* Insert a new slide - CTRL+
* Switch to the next pane (clockwise) - F6
* Switch to the previous pane (counterclockwise) - SHIFT+F6
* Make a duplicate of the current slide - CTRL+D
* Start a slide show - F5
* Promote a paragraph - ALT+SHIFT+LEFT ARROW
* Demote a paragraph - ALT+SHIFT+RIGHT ARROW
* Apply subscript formatting - CTRL+EQUAL SIGN (=)
* Apply superscript formatting - CTRL+PLUS SIGN (+)
* Open the Font dialog box - CTRL+T
* Repeat your last action - F4 or CTRL+Y
* Find - CTRL+F
* View guides - CTRL+G
* Delete a word - CTRL+BACKSPACE
* Capitalize - SHIFT+F3
* Bold - CTRL+B
* Italicize - CTRL+I
* Insert a hyperlink - CTRL+K
* Select all - CTRL+A
* Copy - CTRL+C
* Paste - CTRL+V
* Undo - CTRL+Z
* Save - CTRL+S
* Print - CTRL+P
* Open - CTRL+O
It should be noted that the majority of these shortcuts work in every Office application, not just PowerPoint.
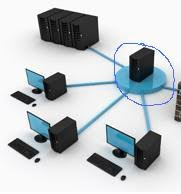
Block Ads
You know those ads that take over your entire screen? Or the ones that intrusively play music, alerting everyone around you that you've visited a website that is probably not work-related? How about those ads that leave behind tracking cookies so they can monitor your internet surfing behavior? These are the ads that make you scared to surf the internet. Fortunately, you can avoid them.
Ad blockers are among the most popular browser extensions around. But if you use several browsers on several PCs, keeping everything in sync and installing all those plug-ins can be a pain, especially when you could be blocking ads at a higher level.
It's not hard to block ads long before they reach your browser, you just need to set up an IP-blocking list (the same technology your browser-based blocker is using) either on your PC or through your router.
Ad blockers are among the most popular browser extensions around. But if you use several browsers on several PCs, keeping everything in sync and installing all those plug-ins can be a pain, especially when you could be blocking ads at a higher level.
It's not hard to block ads long before they reach your browser, you just need to set up an IP-blocking list (the same technology your browser-based blocker is using) either on your PC or through your router.
Identify a Phishing Scam
Hold on to your passwords if you want to stay safe on the internet. Of course, you need those passwords to access your bank, your e-mail and sites where you connect with friends. There are people out to trick you into giving those private codes away using a scam called "phishing." Let's look at how to identify and avoid falling for one yourself.
The strange name sounds a lot like the fishing you do in a lake with a pole. That's because it's a similar process: phishers apply bait and wait for a bite. They want you to be the fish.
These scams find ways to get you to a page that looks like the login to a financial institution or other site where knowing your credentials can benefit them in some way. Many times the "hook" comes in the form of an e-mail that appears to be from a trusted source. Also in the e-mail is a call to click a link to go to a site that is made to look like the one you know.
Another common phishing scheme, especially on social networks, is to take advantage of messaging systems built into the products. The messages may even come from trusted friends, who have themselves fallen pray to the scam.
Once you are on the phishing site, if you type your login information, it will be sent to the bad guys, even though it looks just like a site you trust.
Read on to learn some ways to identify a scam before you fall for it.
Too Good To Be True
Your bank just sent you an e-mail. You open it up and the bank claims to have found an error in your favor. "Click here" to claim the money which is rightfully yours! The old saying still has resonance in this connected age. If it sounds too good to be true, it probably is.
Your friend may be touting a get-rich-quick scheme. Even if this friend usually shares completely reliable information, be wary. Your friend may have fallen victim to a scam himself. If you have his phone number, pick up the phone and get to the bottom of it. He may appreciate you alerting him to the scam.
Since we've all become fairly resistant to this "too good" scam, many phishers use the opposite approach. If it sounds too bad to be true, such as an unexpected large payment from your account being processed by your bank, watch out. The scammers are preying on your desire to fix the problem immediately.
The same goes for unexpected payments or charges with online wallet services like Paypal. When it comes to your money, especially, you can't be too skeptical. Read on for other ways to identify whether there's a scammer on the other end of that login form.
Look at the URL
This may get a little techy, but it's something any internet user should learn. The URL (Uniform Resource Locator), which is the web page's full address, is a telling hint toward whether you're being scammed.
Your location bar is usually up at the top of the window you use for web browsing. The text inside starts with http:// or https://. The part that comes immediately after that is the host name, like /wired.com/. Sometimes, instead it has extra words up front, like /howto.wired.com/. That's called a sub-domain.
Whoever owns the main .com (or .net, .org, etc.) can make as many sub-domains as they want. Scammers use a simple trick to include your bank's name in front of their own web site name.
Let's say your bank's website is yourbank.com. A scammer might use yourbank.securebank.com, which looks pretty good. But remember, your bank can own anything ending in .yourbank.com. But whoever owns securebank.com (the scammer in this case) can put anything in front of securebank.com, including the name of your bank.
Using the URL to identify the scam means you have to understand the difference between securebank.yourbank.com and yourbank.securebank.com. If they look the same to you, know that makes you extra vulnerable. Just when you thought it couldn't get worse: often the scammers get really devious and use yourbank.com.securebank.com. The URL begins with your bank's complete web site name, but it's still a scam!
Some browsers identify the main part of the host name by bolding it in the location bar. That can make it easier to figure out whether or not you're looking at the real site. Even with the visual aid, it's still all too easy to misread the text in the location bar.
Login at the Site Itself
At this point, you have an inkling you're being phished, yet you also want to know if there really is a deposit waiting for your account. If it sounds too good to be true, and you aren't able to decipher whether it's the real URL, it's time to go straight to the source.
You need to visit your bank, or whichever site this is, directly. Don't click links in e-mails or messages, but preferably type the address of the site you usually use into the location bar. Alternatively, you can search for the name of the bank and click the search result.
Once you are on the site itself, log in there. Doing this will ensure that you are really on the correct website and not sending your credentials to a third party. When you have logged in, look to verify the information you were told in the potential phishing scam. For example, if your bank e-mailed you about a bounced check, wouldn't there be some sign of that on the site itself, too?
If you still aren't sure, you can go old school: Pick up the phone. If the site is a financial institution, there's got to be a way to call them. Remember to get the number from the real site, not from the site you visit by clicking a link.
Following this and other tips in this article should keep you safe from phishing scams. Healthy skepticism and a little technical know-how go a long way to keeping your personal data secure.
The strange name sounds a lot like the fishing you do in a lake with a pole. That's because it's a similar process: phishers apply bait and wait for a bite. They want you to be the fish.
These scams find ways to get you to a page that looks like the login to a financial institution or other site where knowing your credentials can benefit them in some way. Many times the "hook" comes in the form of an e-mail that appears to be from a trusted source. Also in the e-mail is a call to click a link to go to a site that is made to look like the one you know.
Another common phishing scheme, especially on social networks, is to take advantage of messaging systems built into the products. The messages may even come from trusted friends, who have themselves fallen pray to the scam.
Once you are on the phishing site, if you type your login information, it will be sent to the bad guys, even though it looks just like a site you trust.
Read on to learn some ways to identify a scam before you fall for it.
Too Good To Be True
Your bank just sent you an e-mail. You open it up and the bank claims to have found an error in your favor. "Click here" to claim the money which is rightfully yours! The old saying still has resonance in this connected age. If it sounds too good to be true, it probably is.
Your friend may be touting a get-rich-quick scheme. Even if this friend usually shares completely reliable information, be wary. Your friend may have fallen victim to a scam himself. If you have his phone number, pick up the phone and get to the bottom of it. He may appreciate you alerting him to the scam.
Since we've all become fairly resistant to this "too good" scam, many phishers use the opposite approach. If it sounds too bad to be true, such as an unexpected large payment from your account being processed by your bank, watch out. The scammers are preying on your desire to fix the problem immediately.
The same goes for unexpected payments or charges with online wallet services like Paypal. When it comes to your money, especially, you can't be too skeptical. Read on for other ways to identify whether there's a scammer on the other end of that login form.
Look at the URL
This may get a little techy, but it's something any internet user should learn. The URL (Uniform Resource Locator), which is the web page's full address, is a telling hint toward whether you're being scammed.
Your location bar is usually up at the top of the window you use for web browsing. The text inside starts with http:// or https://. The part that comes immediately after that is the host name, like /wired.com/. Sometimes, instead it has extra words up front, like /howto.wired.com/. That's called a sub-domain.
Whoever owns the main .com (or .net, .org, etc.) can make as many sub-domains as they want. Scammers use a simple trick to include your bank's name in front of their own web site name.
Let's say your bank's website is yourbank.com. A scammer might use yourbank.securebank.com, which looks pretty good. But remember, your bank can own anything ending in .yourbank.com. But whoever owns securebank.com (the scammer in this case) can put anything in front of securebank.com, including the name of your bank.
Using the URL to identify the scam means you have to understand the difference between securebank.yourbank.com and yourbank.securebank.com. If they look the same to you, know that makes you extra vulnerable. Just when you thought it couldn't get worse: often the scammers get really devious and use yourbank.com.securebank.com. The URL begins with your bank's complete web site name, but it's still a scam!
Some browsers identify the main part of the host name by bolding it in the location bar. That can make it easier to figure out whether or not you're looking at the real site. Even with the visual aid, it's still all too easy to misread the text in the location bar.
Login at the Site Itself
At this point, you have an inkling you're being phished, yet you also want to know if there really is a deposit waiting for your account. If it sounds too good to be true, and you aren't able to decipher whether it's the real URL, it's time to go straight to the source.
You need to visit your bank, or whichever site this is, directly. Don't click links in e-mails or messages, but preferably type the address of the site you usually use into the location bar. Alternatively, you can search for the name of the bank and click the search result.
Once you are on the site itself, log in there. Doing this will ensure that you are really on the correct website and not sending your credentials to a third party. When you have logged in, look to verify the information you were told in the potential phishing scam. For example, if your bank e-mailed you about a bounced check, wouldn't there be some sign of that on the site itself, too?
If you still aren't sure, you can go old school: Pick up the phone. If the site is a financial institution, there's got to be a way to call them. Remember to get the number from the real site, not from the site you visit by clicking a link.
Following this and other tips in this article should keep you safe from phishing scams. Healthy skepticism and a little technical know-how go a long way to keeping your personal data secure.
Monday, November 23, 2009
Delete Browser Cookies
The web knows who you are. It knows what which sites you like, what you search for and where you spend your time. By collating these and other bits of data, it's not hard to figure out quite a bit about you.
If that makes you nervous, you need to learn how to get rid of cookies and browse privately, without leaving a digital fingerprint everywhere you go.
Cookies are like digital leeches that websites inject into your web browser to collect and remember data. In some cases, cookies are quite benign and simple. In fact, cookies are what websites use to remember that you're logged into a particular site. But some cookies are less benign, tracking everything you search for and sending that data back to a central server.
Ostensibly such data is anonymized, but as several sets of leaked data have demonstrated: despite the anonymizing it is often easy to match users back to their data. Grat tool for clean cookes is Ccleaner is free and works very good. http://www.ccleaner.com/
If that makes you nervous, you need to learn how to get rid of cookies and browse privately, without leaving a digital fingerprint everywhere you go.
Cookies are like digital leeches that websites inject into your web browser to collect and remember data. In some cases, cookies are quite benign and simple. In fact, cookies are what websites use to remember that you're logged into a particular site. But some cookies are less benign, tracking everything you search for and sending that data back to a central server.
Ostensibly such data is anonymized, but as several sets of leaked data have demonstrated: despite the anonymizing it is often easy to match users back to their data. Grat tool for clean cookes is Ccleaner is free and works very good. http://www.ccleaner.com/
New Worm Attacks iPhones, Targets Mobile Banking
A second iPhone worm is in the wild, and unlike the jokey Australian worm authored by hacker prankster Ikee two weeks ago, this one is dangerous.
Unlike Ikee’s hack, which merely rick-rolled owners of infected iPhones, the new Dutch variant targets customers of the bank ING. When triggered, the worm redirects users visiting the banking site to an address in Lithuania which shows a fake login screen for ING online banking. It is essentially a phishing attack run on compromised iPhones.
The panic that will inevitably spread from this story is unjustified. First, if you are a regular iPhone customer you are safe, even if you are in the Netherlands. This is because, like the Ikee hack before it, the new worm will only work on a jailbroken, or hacked iPhone. Further, you will have to explicitly install SSH remote access, and then you will have to leave the root password at its default, which is alpine.
If that means nothing to you, you don’t have any reason to worry. If that does mean something to you, shame on you! You should go change that password right now.
And don’t forget, you’ll also need to live in Holland and to be a customer of the ING bank for this to work. This could explain why this “security breach”, according to the BBC, has only affected a few people: “The number of infected phones was thought to be in the hundreds rather than thousands.” And how does it spread itself? “The worm could jump from phone to phone among owners using the same wi-fi hotspot.”
While we shouldn’t ignore the threat of malware to our increasingly powerful and connected mobile devices, neither should we panic. The news of a genuine iPhone-killing piece of software seems to be treated with the same glee as news of a virus for the Mac.
Unlike Ikee’s hack, which merely rick-rolled owners of infected iPhones, the new Dutch variant targets customers of the bank ING. When triggered, the worm redirects users visiting the banking site to an address in Lithuania which shows a fake login screen for ING online banking. It is essentially a phishing attack run on compromised iPhones.
The panic that will inevitably spread from this story is unjustified. First, if you are a regular iPhone customer you are safe, even if you are in the Netherlands. This is because, like the Ikee hack before it, the new worm will only work on a jailbroken, or hacked iPhone. Further, you will have to explicitly install SSH remote access, and then you will have to leave the root password at its default, which is alpine.
If that means nothing to you, you don’t have any reason to worry. If that does mean something to you, shame on you! You should go change that password right now.
And don’t forget, you’ll also need to live in Holland and to be a customer of the ING bank for this to work. This could explain why this “security breach”, according to the BBC, has only affected a few people: “The number of infected phones was thought to be in the hundreds rather than thousands.” And how does it spread itself? “The worm could jump from phone to phone among owners using the same wi-fi hotspot.”
While we shouldn’t ignore the threat of malware to our increasingly powerful and connected mobile devices, neither should we panic. The news of a genuine iPhone-killing piece of software seems to be treated with the same glee as news of a virus for the Mac.
Thursday, November 19, 2009
Consejos para hacer compras en internet
Hoy en día los consumidores tienen acceso a miles de productos desde su casa. El internet abrió las puestas a todo tipo de bienes y servicios, desde provisiones, carros, seguros y hasta préstamos hipotecarios, que se pueden comprar electrónicamente.
1. Haga sus compras en sitios seguros
¿Cómo se pueden identificar los sitios seguros? Tales direcciones electrónicas utilizan tecnología que permite el intercambio de información codificada de computadora a computadora. De esa manera, datos como números de tarjeta de crédito, se transmiten de manera segura y lejos del alcance de criminales cibernéticos. Los únicos que pueden decodificar esa información son aquellos que tienen autorización.
Cómo identificar un sitio seguro:
• Vea la ventana donde se localiza la dirección electrónica del negocio. Ahí encontrará las letras "https://". La "s" al final significa que el sitio es seguro, aunque en ocasiones la "s" sólo aparece en la página de pago.
• Otra manera de saber si el sitio es seguro es observando un candado que se encuentra al pie de la página. Un candado abierto indica que lo más probable es que el sitio no es seguro.
• El tercer indicador es una llave al pie de la página. Una llave entera significa un sitio seguro.
2. Conozca el sitio bien antes de comprar
Procure hacer compras en sitios que usted ya conoce. De otra manera, investigue antes de comprar. Si decide hacerlo, pruebe primero con producto barato para asegurarse de que el sitio es confiable.
Usted puede conocer la integridad de un negocio por medio de asociaciones como el Better Bussiness Bureau (agencia de protección al consumidor) o de la oficina del fiscal local o federal. Trate de verificar la dirección de un negocio con la ayuda de algún amigo o miembro de familia que viva en la misma ciudad donde se localiza la compañía. Recuerde, cualquiera puede tener una página de internet.
3. Lea la política de privacidad y seguridad del sitio
Todo negocio electrónico confiable ofrece información sobre su transacción. Por lo general puede conocer esa información en una sección llamada "Privacy Policy". Es ahí donde conocerá el destino de sus datos personales: ¿serán vendidos a una tercera persona o a un negocio afiliado? En el caso de que vendan, ¿se requiere a las compañías compradoras de no contactar a los consumidores? Si no, lo más probable es que usted recibirá correspondencia electrónica "spam" (masiva) o hasta mercadotecnia por correspondencia tradicional o llamadas por teléfono.
Usted puede conocer cómo el negocio obtuvo su información y si la comparte con otras compañías. La política de la compañía está disponible en la sección "Policy Notice" o bajo el nombre de "Security Policy". Busque negocios que pertenezcan a un programa que identifica a las compañías cibernéticas que voluntariamente realizan políticas favorables a la protección de la privacidad. Tales programas incluyen a TRUSTe (www.truste.org) y BBBonline (www.bbbonline.org).
4. ¿Cuál es el medio más seguro para hacer sus compras por internet: tarjetas de crédito, débito, en efectivo o cheques?
La manera más segura para hacer comprar por internet es con una tarjeta de crédito, ya que de esa forma el consumidor está protegido por la ley federal Fair Credit Billing Act.
El usar cheques durante una transacción por internet lo deja vulnerable al fraude bancario. El uso de un cheque de caja (cashierís check) o una orden de pago (money order) lo deja desprotegido.
5. Jamás utilice su número de Seguro Social por internet
Ninguna compra requiere el uso de su número de Seguro Social. Ningún negocio tiene por qué pedirlo. Usted podría ser víctima de robo de identidad si tales datos caen en manos equivocadas.
6. Proporcione la mínima cantidad de información posible
Hay información clave, como su nombre y dirección, que se debe de proveer al comprar un producto por internet. Sin embargo, es común que un negocio solicite más información. Le podrán preguntar sobre sus hábitos de recreación o sobre sus ingresos, información que se utiliza con fines comerciales, como para mandar correos electrónicos "spam" (masivo), correspondencia directa o llamadas telefónicas.
7. Su contraseña es sólo para usted
La mayoría de los sitios confiables requieren al usuario a inscribirse al sitio (Log-in). Por lo general se requiere un alias y una contraseña. Jamás revele su contraseña a otra persona y cuando escoja una, no utilice combinaciones comunes como la fecha de un cumpleaños, el nombre soltero de su madre, los números de su licencia de manejar o de su Seguro Social. No utilice la misma contraseña en otros sistemas. Las contraseñas más seguras cuentan con 8 dígitos y combinan tanto números como letras.
8. Verifique la dirección del sitio
En la parte superior de la página está un rectángulo que contiene una dirección electrónica (conocido en inglés como el URL o el Uniform Resource Locator). Verifique que usted está en el sitio deseado.
Los criminales cibernéticos han creado sitios extremadamente parecidos a compañías confiables y conocidas. Estos sitos pueden engañar al consumidor y robarlo de números de tarjetas de crédito para realizar compras en su nombre. Sin embargo, esto se puede evitar al verificar la dirección.
9. Mantenga fotocopias de sus transacciones
Al terminar su orden debe de aparecer una página que resume su transacción. Recomendamos que se quede con una copia de ella. Además, imprima la página que contiene el nombre del negocio, la dirección, el número telefónico y los términos legales de su compra. Como precaución, recomendamos que archive esta información hasta que termine el periodo de garantía del producto.
Lo más probable es que usted reciba un correo electrónico de confirmación. Asegure una copia para su archivo e incluya otros mensajes que intercambie con la compañía.
10. Haga sus compras con negocios estadounidenses
Usted está bajo la protección de las leyes federales del consumidor cuando realiza sus compras con compañías estadounidenses. No es lo mismo si usted hace una compra con una compañía extranjera.
11. Conozca los procesos de entrega por correo
La ley requiere a todos los negocios cumplir con la fecha de entrega del producto de acuerdo a los términos de su propia publicidad. Si no se acordó en un tiempo específico, el negocio debe de despachar el producto en menos de 30 días o darle a usted una opción llamada "Option Notice". Esta opción le ofrece la oportunidad de cancelar su orden y recibir un reembolso o acordar con el retraso.
Aquí presentamos algunas preguntas clave que debe de considerar antes de ordenar un producto:
• ¿Existen restricciones de entrega geográficas o de algún otro tipo?
• ¿Hay otras opciones de entrega?
• ¿Quién pagará por los costos del correo?
• ¿Existe algún tipo de seguro para la entrega del producto?
• ¿Cuáles son los costos de entrega? ¿Son justos?
12. Conozca los procedimientos de reembolso, cancelación y quejas
Es un hecho que el consumidor a veces se ve obligado de devolver la mercancía. Verifique las políticas de cancelación y reembolso del negocio.
• ¿Quién paga por los costos del correo?
• ¿Existe algún tiempo límite para cancelar o devolver la mercancía?
• ¿Existe alguna multa por las devoluciones?
• En el caso de devolver el producto, ¿recibirá crédito de tienda o un reembolso directo a su tarjeta de crédito? Si recibe crédito de tienda, pregunte si existe una fecha límite para usarlo.
13. Use su intuición
Evalúe el sitio. Hay algunas ofertas que son demasiadas buenas para ser realidad.
• ¿Hay algo que usted cuestiona en la publicidad de un producto o negocio?
• ¿Están demasiado bajos los precios?
• ¿Es un negocio nuevo?
• ¿El sitio tiene demasiados errores ortográficos y gramaticales?
• ¿Nadie contesta el teléfono de la empresa?
• Un negocio que no provee una dirección postal o física puede ser una señal de precaución.
Si usted tiene alguna sospecha del negocio, no dude en hacer sus compras en otro sitio.
14. Protéjase del robo de identidad
El comercio electrónico indudablemente incrementará los casos de robo de identidad. Hoy en día los delincuentes acuden a tácticas sencillas para robar la identidad de sus víctimas, buscando entre los tambos de basura, robando correspondencia y hasta números de Seguro Social de los archivos de empleadores. Sin embargo, ahora acuden frecuentemente al internet para abrir tarjetas de crédito y hacer sus compras en nombre de sus víctimas.
Los mismos consejos para evitar éstos tipos de robo deben de considerarse para el internet. Pero lo más importante es que usted se familiarice con el negocio y que utilice sólo una tarjeta de crédito.
15. Tenga precaución de firmar electrónicamente
Una ley federal permite oficiar transacciones por medio de una firma electrónica. Por lo general, esta firma es sólo hacer clic en una caja que indica que usted aceptó los términos de compra.
La ley Electronic Signatures in Global and National Commerce Act, también conocida como el E-Sign Act, es compleja. Esta ley dicta que la firma electrónica valida toda transacción electrónica interestatal o extranjera y que no se necesita de documentos tradicionales y físicos.
Los defensores de los derechos del consumidor se oponen a esta ley porque carece de protección contra el fraude. Un ejemplo es que no requiere a compañías cumplir con reglamentos como de seguridad, protección a la privacidad del consumidor y la verificación del cliente.
Otros recursos
Puede conocer más sobre el comercio electrónico en los siguientes sitios:
• www.ifccfbi.gov El centro Internet Fraud Complaint Center de la FBI le permite reportar casos sospechosos de fraude electrónico.
• www.safeshopping.org Consejos para realizar compras por internet. Proveedor: American Bar Association.
• www.bbb.org y www.bbbonline.org Better Business Bureau (BBB) certifica a negocios que protegen la privacidad del consumidor. Usted puede conocer el historial de una compañía o reportar fraudes.
• www.bbb.org/alerts/cybershop.asp El BBB ofrece consejos para realizar sus compras navideñas.
• www.ftc.gov/bcp/menu-internet.htm Federal Trade Commission ofrece consejos para realizar sus compras por internet.
• www.fda.gov/oc/buyonline Un sitio de la U.S. Food and Drug Administration que ofrece consejos para comprar medicina por internet.
• www.fraud.org Información actualizada sobre el fraude cibernético a cargo del National Fraud Administration Center, un programa de National Consumers League.
• www.shopthenet.org El sitio de la Direct Marketing Association. Aquí se provee una lista de negocios que cumplen con la ley federal "Mail or Telephone Order Merchandise Rule", la cual requiere, por ejemplo, que todo negocio haga entrega de sus productos en 30 días.
1. Haga sus compras en sitios seguros
¿Cómo se pueden identificar los sitios seguros? Tales direcciones electrónicas utilizan tecnología que permite el intercambio de información codificada de computadora a computadora. De esa manera, datos como números de tarjeta de crédito, se transmiten de manera segura y lejos del alcance de criminales cibernéticos. Los únicos que pueden decodificar esa información son aquellos que tienen autorización.
Cómo identificar un sitio seguro:
• Vea la ventana donde se localiza la dirección electrónica del negocio. Ahí encontrará las letras "https://". La "s" al final significa que el sitio es seguro, aunque en ocasiones la "s" sólo aparece en la página de pago.
• Otra manera de saber si el sitio es seguro es observando un candado que se encuentra al pie de la página. Un candado abierto indica que lo más probable es que el sitio no es seguro.
• El tercer indicador es una llave al pie de la página. Una llave entera significa un sitio seguro.
2. Conozca el sitio bien antes de comprar
Procure hacer compras en sitios que usted ya conoce. De otra manera, investigue antes de comprar. Si decide hacerlo, pruebe primero con producto barato para asegurarse de que el sitio es confiable.
Usted puede conocer la integridad de un negocio por medio de asociaciones como el Better Bussiness Bureau (agencia de protección al consumidor) o de la oficina del fiscal local o federal. Trate de verificar la dirección de un negocio con la ayuda de algún amigo o miembro de familia que viva en la misma ciudad donde se localiza la compañía. Recuerde, cualquiera puede tener una página de internet.
3. Lea la política de privacidad y seguridad del sitio
Todo negocio electrónico confiable ofrece información sobre su transacción. Por lo general puede conocer esa información en una sección llamada "Privacy Policy". Es ahí donde conocerá el destino de sus datos personales: ¿serán vendidos a una tercera persona o a un negocio afiliado? En el caso de que vendan, ¿se requiere a las compañías compradoras de no contactar a los consumidores? Si no, lo más probable es que usted recibirá correspondencia electrónica "spam" (masiva) o hasta mercadotecnia por correspondencia tradicional o llamadas por teléfono.
Usted puede conocer cómo el negocio obtuvo su información y si la comparte con otras compañías. La política de la compañía está disponible en la sección "Policy Notice" o bajo el nombre de "Security Policy". Busque negocios que pertenezcan a un programa que identifica a las compañías cibernéticas que voluntariamente realizan políticas favorables a la protección de la privacidad. Tales programas incluyen a TRUSTe (www.truste.org) y BBBonline (www.bbbonline.org).
4. ¿Cuál es el medio más seguro para hacer sus compras por internet: tarjetas de crédito, débito, en efectivo o cheques?
La manera más segura para hacer comprar por internet es con una tarjeta de crédito, ya que de esa forma el consumidor está protegido por la ley federal Fair Credit Billing Act.
El usar cheques durante una transacción por internet lo deja vulnerable al fraude bancario. El uso de un cheque de caja (cashierís check) o una orden de pago (money order) lo deja desprotegido.
5. Jamás utilice su número de Seguro Social por internet
Ninguna compra requiere el uso de su número de Seguro Social. Ningún negocio tiene por qué pedirlo. Usted podría ser víctima de robo de identidad si tales datos caen en manos equivocadas.
6. Proporcione la mínima cantidad de información posible
Hay información clave, como su nombre y dirección, que se debe de proveer al comprar un producto por internet. Sin embargo, es común que un negocio solicite más información. Le podrán preguntar sobre sus hábitos de recreación o sobre sus ingresos, información que se utiliza con fines comerciales, como para mandar correos electrónicos "spam" (masivo), correspondencia directa o llamadas telefónicas.
7. Su contraseña es sólo para usted
La mayoría de los sitios confiables requieren al usuario a inscribirse al sitio (Log-in). Por lo general se requiere un alias y una contraseña. Jamás revele su contraseña a otra persona y cuando escoja una, no utilice combinaciones comunes como la fecha de un cumpleaños, el nombre soltero de su madre, los números de su licencia de manejar o de su Seguro Social. No utilice la misma contraseña en otros sistemas. Las contraseñas más seguras cuentan con 8 dígitos y combinan tanto números como letras.
8. Verifique la dirección del sitio
En la parte superior de la página está un rectángulo que contiene una dirección electrónica (conocido en inglés como el URL o el Uniform Resource Locator). Verifique que usted está en el sitio deseado.
Los criminales cibernéticos han creado sitios extremadamente parecidos a compañías confiables y conocidas. Estos sitos pueden engañar al consumidor y robarlo de números de tarjetas de crédito para realizar compras en su nombre. Sin embargo, esto se puede evitar al verificar la dirección.
9. Mantenga fotocopias de sus transacciones
Al terminar su orden debe de aparecer una página que resume su transacción. Recomendamos que se quede con una copia de ella. Además, imprima la página que contiene el nombre del negocio, la dirección, el número telefónico y los términos legales de su compra. Como precaución, recomendamos que archive esta información hasta que termine el periodo de garantía del producto.
Lo más probable es que usted reciba un correo electrónico de confirmación. Asegure una copia para su archivo e incluya otros mensajes que intercambie con la compañía.
10. Haga sus compras con negocios estadounidenses
Usted está bajo la protección de las leyes federales del consumidor cuando realiza sus compras con compañías estadounidenses. No es lo mismo si usted hace una compra con una compañía extranjera.
11. Conozca los procesos de entrega por correo
La ley requiere a todos los negocios cumplir con la fecha de entrega del producto de acuerdo a los términos de su propia publicidad. Si no se acordó en un tiempo específico, el negocio debe de despachar el producto en menos de 30 días o darle a usted una opción llamada "Option Notice". Esta opción le ofrece la oportunidad de cancelar su orden y recibir un reembolso o acordar con el retraso.
Aquí presentamos algunas preguntas clave que debe de considerar antes de ordenar un producto:
• ¿Existen restricciones de entrega geográficas o de algún otro tipo?
• ¿Hay otras opciones de entrega?
• ¿Quién pagará por los costos del correo?
• ¿Existe algún tipo de seguro para la entrega del producto?
• ¿Cuáles son los costos de entrega? ¿Son justos?
12. Conozca los procedimientos de reembolso, cancelación y quejas
Es un hecho que el consumidor a veces se ve obligado de devolver la mercancía. Verifique las políticas de cancelación y reembolso del negocio.
• ¿Quién paga por los costos del correo?
• ¿Existe algún tiempo límite para cancelar o devolver la mercancía?
• ¿Existe alguna multa por las devoluciones?
• En el caso de devolver el producto, ¿recibirá crédito de tienda o un reembolso directo a su tarjeta de crédito? Si recibe crédito de tienda, pregunte si existe una fecha límite para usarlo.
13. Use su intuición
Evalúe el sitio. Hay algunas ofertas que son demasiadas buenas para ser realidad.
• ¿Hay algo que usted cuestiona en la publicidad de un producto o negocio?
• ¿Están demasiado bajos los precios?
• ¿Es un negocio nuevo?
• ¿El sitio tiene demasiados errores ortográficos y gramaticales?
• ¿Nadie contesta el teléfono de la empresa?
• Un negocio que no provee una dirección postal o física puede ser una señal de precaución.
Si usted tiene alguna sospecha del negocio, no dude en hacer sus compras en otro sitio.
14. Protéjase del robo de identidad
El comercio electrónico indudablemente incrementará los casos de robo de identidad. Hoy en día los delincuentes acuden a tácticas sencillas para robar la identidad de sus víctimas, buscando entre los tambos de basura, robando correspondencia y hasta números de Seguro Social de los archivos de empleadores. Sin embargo, ahora acuden frecuentemente al internet para abrir tarjetas de crédito y hacer sus compras en nombre de sus víctimas.
Los mismos consejos para evitar éstos tipos de robo deben de considerarse para el internet. Pero lo más importante es que usted se familiarice con el negocio y que utilice sólo una tarjeta de crédito.
15. Tenga precaución de firmar electrónicamente
Una ley federal permite oficiar transacciones por medio de una firma electrónica. Por lo general, esta firma es sólo hacer clic en una caja que indica que usted aceptó los términos de compra.
La ley Electronic Signatures in Global and National Commerce Act, también conocida como el E-Sign Act, es compleja. Esta ley dicta que la firma electrónica valida toda transacción electrónica interestatal o extranjera y que no se necesita de documentos tradicionales y físicos.
Los defensores de los derechos del consumidor se oponen a esta ley porque carece de protección contra el fraude. Un ejemplo es que no requiere a compañías cumplir con reglamentos como de seguridad, protección a la privacidad del consumidor y la verificación del cliente.
Otros recursos
Puede conocer más sobre el comercio electrónico en los siguientes sitios:
• www.ifccfbi.gov El centro Internet Fraud Complaint Center de la FBI le permite reportar casos sospechosos de fraude electrónico.
• www.safeshopping.org Consejos para realizar compras por internet. Proveedor: American Bar Association.
• www.bbb.org y www.bbbonline.org Better Business Bureau (BBB) certifica a negocios que protegen la privacidad del consumidor. Usted puede conocer el historial de una compañía o reportar fraudes.
• www.bbb.org/alerts/cybershop.asp El BBB ofrece consejos para realizar sus compras navideñas.
• www.ftc.gov/bcp/menu-internet.htm Federal Trade Commission ofrece consejos para realizar sus compras por internet.
• www.fda.gov/oc/buyonline Un sitio de la U.S. Food and Drug Administration que ofrece consejos para comprar medicina por internet.
• www.fraud.org Información actualizada sobre el fraude cibernético a cargo del National Fraud Administration Center, un programa de National Consumers League.
• www.shopthenet.org El sitio de la Direct Marketing Association. Aquí se provee una lista de negocios que cumplen con la ley federal "Mail or Telephone Order Merchandise Rule", la cual requiere, por ejemplo, que todo negocio haga entrega de sus productos en 30 días.
Thursday, October 29, 2009
Survey Shows Parents Would Rather Talk Drugs Than Science or Math
There is a point in every family when it’s time for the talk. No, not that talk. Not that one either. I’m talking about the science-and-math talk. The kind of talk that should happen every time your child is having trouble or even just working on homework. Most parents, having been through primary school themselves at some point, have a difficult time with this talk. In fact, according to a recent survey conducted through the Intel Corporation, parents are more comfortable talking with their kids about drugs than about science and math.
Some key points from the survey:
* More than half (53 percent) of parents of teenagers admit that they have trouble helping their children with math and science homework.
* Nearly a quarter of parents (23 percent) who admit to being less involved in their child’s math and science education than they would like say their own lack of knowledge in these subjects is a key barrier.
* Another 26 percent of parents who are less involved than they would like wish there were a one-stop shop with materials to refresh their existing, but unused math and science knowledge so they can better help their kids.
Talking about drugs is easier for parents because it’s a vague subject. It doesn’t have much depth to it. You can get the message across in just a couple of short sentences, or an example of someones’ life gone wrong thanks to the influence of drugs. Not to mention, it’s a talk that almost every competent parent has with their child at some point in their lives, right up there with the good ol’ sex talk.
Science and math are not vague subjects. Not only is there extreme depth to be found, but there is commonly a generational gap between the parent and the child. Science and math haven’t changed, but the amount of knowledge and the understanding has. We know more as adults than when we were children, but we have to relate to them on a child’s level, rather than on an adult-level understanding of the material. This is where it becomes difficult for parents. Shelly Esque, vice president of Intel’s corporate-affairs group, explains the challenge:
Our survey points to a difficult reality for our nation’s parents: While they may recognize the importance of math and science, they are unable to engage with their children around these subjects due to limited understanding of the topics and scarcity of resources to help. We need to help parents help their kids make the best choices, including taking math and science courses so they are prepared to succeed.
Even though 98 percent of parents believe that science and math are critical to the future of the country, and 91 percent believe that parental involvement is key to their children’s success, parents are still having trouble talking to their children about science and math. Sure, it’s easy to express the importance of the subjects, but when it comes down to actually doing something — that is where we’re lacking. Even I have trouble helping with math and science sometimes. Not because I’m not knowledgeable, but because it’s hard to transfer my knowledge to that of an 8-year-old.
The problem is, parents recognize that math and science are critical to their child’s future success, but they also realize that speaking to their children about drugs and alcohol is critical to their child’s survival. Especially when it comes to talking to teenagers, it’s hard enough just saying hello to them, much less trying to connect with them on their schoolwork. So the drug talk is always easier.
What parents need, and — as the survey data mentioned above shows — they know they need. is help. Normally I’d say that it’s all up to the parents, and they should work on the effectiveness without outside intervention.
However, when a company like Intel is willing to step up and put in the time and resources to come up with solutions to assist parents in connecting with their children on math and science, I’ll make an exception. Through its initiatives it’s looking to bridge the gap and create tools that parents can use to better understand what their children are working on and what they can do to help. Shelly Esque again:
Over the past decades, Intel has worked extensively with teachers, students, communities and governments to help inspire and prepare the next generation of innovators with a solid math and science education. We haven’t, though, worked with parents, who we think are a critical piece of the education equation. Our goal in releasing the results of this survey is to raise awareness among parents that they aren’t alone in their challenges so they feel more confident seeking out assistance to encourage their kids to take an interest in math and science, and we hope resource providers will come forward to help them.
Parents, take note. When a company like Intel is stepping in to provide a means to assist you in bridging the educational gap with your children, take full advantage. To that point, if you have the resources to help, feel free to do so. While it’s important that your kids grow up drug-free and healthy, it’s just as important that they grow up educated as well. You can almost guarantee that the less you focus on their education, the more you are going to be focusing on the drug talks.
To learn more about the Intel Education Initiative, visit www.intel.com/education. To join Intel’s community for change in global education, visit www.inspiredbyeducation.com.
Some key points from the survey:
* More than half (53 percent) of parents of teenagers admit that they have trouble helping their children with math and science homework.
* Nearly a quarter of parents (23 percent) who admit to being less involved in their child’s math and science education than they would like say their own lack of knowledge in these subjects is a key barrier.
* Another 26 percent of parents who are less involved than they would like wish there were a one-stop shop with materials to refresh their existing, but unused math and science knowledge so they can better help their kids.
Talking about drugs is easier for parents because it’s a vague subject. It doesn’t have much depth to it. You can get the message across in just a couple of short sentences, or an example of someones’ life gone wrong thanks to the influence of drugs. Not to mention, it’s a talk that almost every competent parent has with their child at some point in their lives, right up there with the good ol’ sex talk.
Science and math are not vague subjects. Not only is there extreme depth to be found, but there is commonly a generational gap between the parent and the child. Science and math haven’t changed, but the amount of knowledge and the understanding has. We know more as adults than when we were children, but we have to relate to them on a child’s level, rather than on an adult-level understanding of the material. This is where it becomes difficult for parents. Shelly Esque, vice president of Intel’s corporate-affairs group, explains the challenge:
Our survey points to a difficult reality for our nation’s parents: While they may recognize the importance of math and science, they are unable to engage with their children around these subjects due to limited understanding of the topics and scarcity of resources to help. We need to help parents help their kids make the best choices, including taking math and science courses so they are prepared to succeed.
Even though 98 percent of parents believe that science and math are critical to the future of the country, and 91 percent believe that parental involvement is key to their children’s success, parents are still having trouble talking to their children about science and math. Sure, it’s easy to express the importance of the subjects, but when it comes down to actually doing something — that is where we’re lacking. Even I have trouble helping with math and science sometimes. Not because I’m not knowledgeable, but because it’s hard to transfer my knowledge to that of an 8-year-old.
The problem is, parents recognize that math and science are critical to their child’s future success, but they also realize that speaking to their children about drugs and alcohol is critical to their child’s survival. Especially when it comes to talking to teenagers, it’s hard enough just saying hello to them, much less trying to connect with them on their schoolwork. So the drug talk is always easier.
What parents need, and — as the survey data mentioned above shows — they know they need. is help. Normally I’d say that it’s all up to the parents, and they should work on the effectiveness without outside intervention.
However, when a company like Intel is willing to step up and put in the time and resources to come up with solutions to assist parents in connecting with their children on math and science, I’ll make an exception. Through its initiatives it’s looking to bridge the gap and create tools that parents can use to better understand what their children are working on and what they can do to help. Shelly Esque again:
Over the past decades, Intel has worked extensively with teachers, students, communities and governments to help inspire and prepare the next generation of innovators with a solid math and science education. We haven’t, though, worked with parents, who we think are a critical piece of the education equation. Our goal in releasing the results of this survey is to raise awareness among parents that they aren’t alone in their challenges so they feel more confident seeking out assistance to encourage their kids to take an interest in math and science, and we hope resource providers will come forward to help them.
Parents, take note. When a company like Intel is stepping in to provide a means to assist you in bridging the educational gap with your children, take full advantage. To that point, if you have the resources to help, feel free to do so. While it’s important that your kids grow up drug-free and healthy, it’s just as important that they grow up educated as well. You can almost guarantee that the less you focus on their education, the more you are going to be focusing on the drug talks.
To learn more about the Intel Education Initiative, visit www.intel.com/education. To join Intel’s community for change in global education, visit www.inspiredbyeducation.com.
Tuesday, October 27, 2009
Cybercrooks Trick Gawker Into Serving Malware-Laced Ad
Remember when the global economic crisis was supposed to drive legions of desperate, unemployed computer programmers into cybercrime? It turns out the real threat comes from unemployed advertising agents.
Scammers posing as the well-known ad agency Spark-SMG tricked Gawker Media into running a fake Suzuki ad last week that served malicious code, according to a report in Silicon Alley Insider. A similar scam hit the New York Times in September. Unlike the newspaper, Gawker has released the e-mails it exchanged with the scammers, and the messages show just how confidently the perps navigated the ad-buy process.
“We are only interested in standard IAB banner sizes right now as that’s what we have sign off for,” wrote fake person George Delarosa, at one point in the negotiations. “Please whip up a proposal and let’s try and get a rush on getting something going as we are in need of some major imps by the end of the month as we are under-delivering on our monthly impression levels for September.”
I’d rather voluntarily install the malware then read that paragraph again. But it does show that the scamsters — who are probably behind the Times attack as well — know exactly what they’re doing. In addition to the authentic prose, the crooks backed their play with a working phone number in a Chicago area code, where the real Spark is based, and a copycat domain name.
“Whoever it is definitely worked in online ad sales at some point ,” an anonymous Gawker salesperson wrote the Insider.
With legitimate ad sales in a slump industrywide, malware-laced banners and, more commonly, just plain deceptive ads are enjoying way too much access to legitimate outlets these days, sometimes delivered through third-party ad networks, and sometimes through direct sales like in the Gawker and Times attacks.
The problem has grown so large that New York ad company Epic Advertising has hired a former FBI cybercrime agent to head a division that scrutinizes potential advertisers. The company is hoping to distinguish itself in the market with a commitment not to run malware, dubious testimonials and ads linking to fake news articles.
“All ads are previewed in advance with the sales team, then they have to go through Compliance to make sure they don’t say anything funky,” says Epic’s E.J. Hilbert, who worked against Eastern European cybercrooks while in the Bureau. “We are the watchdogs and the hound dogs. I think like a bad guy. I think like a guy who’s going to manipulate these situations, and help to devise a way to make sure that we don’t fall for it.”
For those without G-men on staff, a few minutes of sleuthing might prevent gaffes like Gawker’s. While Gawker’s salesperson says the company did all it could to scrutinize the fake Suzuki ad, a quick phone call to a known and trusted number for the real Spark would likely have put the kibosh on the attack before it began.
The ad ran for “less than 5 days last week,” said Gawker’s James Del, in an e-mail to Threat Level. “This was a very malicious piece of code that seemingly took advantage of unpatched Adobe software, though we don’t have details on how exactly that worked. It was not a ‘trick’ ad, wherein users were prompted to install something … It simply strong armed it’s way through a vulnerability and infected the computer.
“This isn’t a worm that goes unnoticed,’ Del added. “It would have crippled the user’s computer in a few moments, based on the reports we received. There would have been pop ups, freezing, and multiple file downloads taking place.”
—
Scammers posing as the well-known ad agency Spark-SMG tricked Gawker Media into running a fake Suzuki ad last week that served malicious code, according to a report in Silicon Alley Insider. A similar scam hit the New York Times in September. Unlike the newspaper, Gawker has released the e-mails it exchanged with the scammers, and the messages show just how confidently the perps navigated the ad-buy process.
“We are only interested in standard IAB banner sizes right now as that’s what we have sign off for,” wrote fake person George Delarosa, at one point in the negotiations. “Please whip up a proposal and let’s try and get a rush on getting something going as we are in need of some major imps by the end of the month as we are under-delivering on our monthly impression levels for September.”
I’d rather voluntarily install the malware then read that paragraph again. But it does show that the scamsters — who are probably behind the Times attack as well — know exactly what they’re doing. In addition to the authentic prose, the crooks backed their play with a working phone number in a Chicago area code, where the real Spark is based, and a copycat domain name.
“Whoever it is definitely worked in online ad sales at some point ,” an anonymous Gawker salesperson wrote the Insider.
With legitimate ad sales in a slump industrywide, malware-laced banners and, more commonly, just plain deceptive ads are enjoying way too much access to legitimate outlets these days, sometimes delivered through third-party ad networks, and sometimes through direct sales like in the Gawker and Times attacks.
The problem has grown so large that New York ad company Epic Advertising has hired a former FBI cybercrime agent to head a division that scrutinizes potential advertisers. The company is hoping to distinguish itself in the market with a commitment not to run malware, dubious testimonials and ads linking to fake news articles.
“All ads are previewed in advance with the sales team, then they have to go through Compliance to make sure they don’t say anything funky,” says Epic’s E.J. Hilbert, who worked against Eastern European cybercrooks while in the Bureau. “We are the watchdogs and the hound dogs. I think like a bad guy. I think like a guy who’s going to manipulate these situations, and help to devise a way to make sure that we don’t fall for it.”
For those without G-men on staff, a few minutes of sleuthing might prevent gaffes like Gawker’s. While Gawker’s salesperson says the company did all it could to scrutinize the fake Suzuki ad, a quick phone call to a known and trusted number for the real Spark would likely have put the kibosh on the attack before it began.
The ad ran for “less than 5 days last week,” said Gawker’s James Del, in an e-mail to Threat Level. “This was a very malicious piece of code that seemingly took advantage of unpatched Adobe software, though we don’t have details on how exactly that worked. It was not a ‘trick’ ad, wherein users were prompted to install something … It simply strong armed it’s way through a vulnerability and infected the computer.
“This isn’t a worm that goes unnoticed,’ Del added. “It would have crippled the user’s computer in a few moments, based on the reports we received. There would have been pop ups, freezing, and multiple file downloads taking place.”
—
Thursday, October 22, 2009
7 Reasons to Avoid Windows 7
Windows 7, which hits stores in October, is shaping up to be the best version of Microsoft’s widely used operating system yet.
But nothing’s perfect. Windows 7, like any product, has flaws — some of them big ones. Wired.com on Tuesday laid out a list of good reasons to upgrade to Windows 7, including an enhanced user interface, improved compatibility with newer hardware and a seamless entertainment experience. (For even more background, see our first look at Windows 7.)
Now let’s look at the other side of the story: The reasons you might consider skipping this upgrade altogether.
Upgrading From Windows XP Requires a Clean Install
If you’re a Windows XP user, upgrading isn’t as easy as inserting a disc and running the installation. Instead, you must back up your applications and files, wipe your hard drive and perform a clean install of Windows 7. After getting Windows 7 up and running, you must either manually reinstall your software and repurpose your file library or trust Microsoft’s Easy File Transfer to migrate your files for you.
We don’t see this as much of a headache, because data backups should be performed regardless of whether you’re switching to a new OS. Plus, a fresh install is preferable to ensure clean performance. But we understand why this would bug many XP users. For one, it’s time-consuming. For another, many are sensitive about their data, and they don’t trust Microsoft. (We don’t blame them.) Third, if XP is working fine for you, why fix something that isn’t broken?
Vista users, on the other hand, can upgrade to Windows 7 without a clean install. They might as well climb out of that train wreck, since it’s easy.
The Upgrade Is Expensive
Windows 7 isn’t cheap. Pricing varies based on the version you choose, but you’ll be paying at least $120 to upgrade from XP or Vista. And if you don’t already own a copy of a Windows OS, you must pay the full price of at least $200 for Windows 7.
In the software market, $120 isn’t ridiculous for an upgrade. Apple’s Mac OS X Leopard costs $130, for instance. However, Apple plans to sell its next OS, Mac OS X Snow Leopard, for $30 to current Leopard users. This Apple power move alone makes Windows 7’s pricing look pretty steep.
It’ll Cost You Time, Too
The customers most likely to opt against upgrading to Windows 7 because of money are businesses. Joe Ansel, owner of a company that plans development of science centers, wrote in an e-mail stating his reasons for not upgrading to Windows 7: “Upgrades cost us time and money as we find ourselves playing with our computers to make them do the things they used to do seamlessly — while the phone never stops ringing and you’re getting 60 e-mails a day. Make no mistake, as a business owner, the cost of the upgrade itself is nothing compared to the lost wages trying to get the new OS to do what the old one did.”
Ansel added that companies running obscure software will also feel disinclined to switch. Microsoft promises Windows 7 will support almost every piece of software compatible with XP, and in the few cases it doesn’t, there’s an XP virtualization mode ensuring backward compatibility. Still, companies invest thousands of dollars to create a stable IT environment, and it’s understandable why they wouldn’t wish to upset their non-Apple cart.
It’s Still Windows
Despite delivering an intuitive, modern interface in Windows 7, this OS is still Windows. In our first look at Windows 7, we complained about the OS’s inability to recognize an Adobe AIR file followed by its failure to search for software to run the file.
Also, Windows 7 doesn’t immediately know what to do with some pretty obvious tasks. When you insert a thumb drive, for example, you must tell Windows 7 what to do with it (i.e. open the folder and view the files) and customize a setting to get the OS to automatically behave that way. In short, when getting started you’ll have to do a lot of tweaking and customizing to get moving smoothly. That’s unfortunately an experience all Windows users are accustomed to — things don’t “just work.”
Security Isn’t Automatically Better
Computerworld’s Steven Vaughan-Nichols stands firm that Windows 7 won’t change anything from a security perspective: “Windows 7 still has all the security of a drunken teenager in a sports car,” he wrote. “Millions of lazy Windows users are the reason why the internet is a mess. If you already do all the right things to keep XP running safely, you’re not going to get any safer by buying Windows 7.”
Good point. Because Windows 7 is still Windows, you’re again the primary target of attack for hackers and virus coders. Therefore, it’s up to you to protect yourself with anti-virus software and running update patches to keep the OS as secure as possible. (Compare this experience to Mac OS X Leopard, for which many don’t even run anti-virus software, because it’s more secure out-of-the-box compared to Windows.) Though Windows 7 does deliver some security enhancements, such as data encryption for thumb drives, and a feature for IT administrators to control which applications can run on a corporate network, these are not general security improvements that change much for the overall user experience.
Built-In Support for Egregious Hardware-Based DRM
Paranoid XP users won’t wish to upgrade to Windows 7 for the same reason they didn’t switch to Vista: Like Vista, Windows 7 includes support for digital rights management technologies that could potentially regulate how you use your media. Though some alarmists have called Microsoft’s DRM “draconian,” the implemented DRM hasn’t proved to bear significant consequences yet.
Ars Technica provides a thorough explanation of the DRM in question. In short, the technologies called Protected Video Path (PVP) and Protected User Mode Audio (PUMA) provide secure playback of video and audio media, respectively. “Little or no media actually demands the use of the protected paths, so on most users’ systems, Windows never invokes them,” wrote Ars Technica’s Peter Bright. “Play back unprotected media on a Vista machine, and the DRM subsystems simply don’t get used.”
Still, there are going to be people cringing in fear that one day PUMA and PVP will screw them over. And for that reason they’ll be sticking with XP — or a totally open OS like Linux.
Snow Leopard Is Almost Here
Apple’s next-generation Snow Leopard is arriving September — a month before Windows 7. Apple is promising its OS will deliver on many of the improvements Microsoft highlights in Windows 7 — 64-bit addressing, improved efficiency with task management on multiple processors, and others. It’s undetermined which OS is better, but from my own perspective as a long-time Mac user, I will say I already prefer the current Mac OS X Leopard to Windows 7. If you’re looking (or willing) to switch to a radically different OS, then OS X Snow Leopard is an option to consider before committing to Windows 7.
Conclusion
Do the cons outweigh the pros? That probably depends on how committed you already are to Windows. If you’re currently using Windows Vista, the upgrade to Windows 7 is a no-brainer. Most of those currently using Windows XP should also upgrade, to take advantage of Windows 7’s usability, enhanced device support, and other features. But if you’re currently using a Linux distribution or a version of Mac OS X, Windows 7 isn’t going to offer much to get you to switch.
But nothing’s perfect. Windows 7, like any product, has flaws — some of them big ones. Wired.com on Tuesday laid out a list of good reasons to upgrade to Windows 7, including an enhanced user interface, improved compatibility with newer hardware and a seamless entertainment experience. (For even more background, see our first look at Windows 7.)
Now let’s look at the other side of the story: The reasons you might consider skipping this upgrade altogether.
Upgrading From Windows XP Requires a Clean Install
If you’re a Windows XP user, upgrading isn’t as easy as inserting a disc and running the installation. Instead, you must back up your applications and files, wipe your hard drive and perform a clean install of Windows 7. After getting Windows 7 up and running, you must either manually reinstall your software and repurpose your file library or trust Microsoft’s Easy File Transfer to migrate your files for you.
We don’t see this as much of a headache, because data backups should be performed regardless of whether you’re switching to a new OS. Plus, a fresh install is preferable to ensure clean performance. But we understand why this would bug many XP users. For one, it’s time-consuming. For another, many are sensitive about their data, and they don’t trust Microsoft. (We don’t blame them.) Third, if XP is working fine for you, why fix something that isn’t broken?
Vista users, on the other hand, can upgrade to Windows 7 without a clean install. They might as well climb out of that train wreck, since it’s easy.
The Upgrade Is Expensive
Windows 7 isn’t cheap. Pricing varies based on the version you choose, but you’ll be paying at least $120 to upgrade from XP or Vista. And if you don’t already own a copy of a Windows OS, you must pay the full price of at least $200 for Windows 7.
In the software market, $120 isn’t ridiculous for an upgrade. Apple’s Mac OS X Leopard costs $130, for instance. However, Apple plans to sell its next OS, Mac OS X Snow Leopard, for $30 to current Leopard users. This Apple power move alone makes Windows 7’s pricing look pretty steep.
It’ll Cost You Time, Too
The customers most likely to opt against upgrading to Windows 7 because of money are businesses. Joe Ansel, owner of a company that plans development of science centers, wrote in an e-mail stating his reasons for not upgrading to Windows 7: “Upgrades cost us time and money as we find ourselves playing with our computers to make them do the things they used to do seamlessly — while the phone never stops ringing and you’re getting 60 e-mails a day. Make no mistake, as a business owner, the cost of the upgrade itself is nothing compared to the lost wages trying to get the new OS to do what the old one did.”
Ansel added that companies running obscure software will also feel disinclined to switch. Microsoft promises Windows 7 will support almost every piece of software compatible with XP, and in the few cases it doesn’t, there’s an XP virtualization mode ensuring backward compatibility. Still, companies invest thousands of dollars to create a stable IT environment, and it’s understandable why they wouldn’t wish to upset their non-Apple cart.
It’s Still Windows
Despite delivering an intuitive, modern interface in Windows 7, this OS is still Windows. In our first look at Windows 7, we complained about the OS’s inability to recognize an Adobe AIR file followed by its failure to search for software to run the file.
Also, Windows 7 doesn’t immediately know what to do with some pretty obvious tasks. When you insert a thumb drive, for example, you must tell Windows 7 what to do with it (i.e. open the folder and view the files) and customize a setting to get the OS to automatically behave that way. In short, when getting started you’ll have to do a lot of tweaking and customizing to get moving smoothly. That’s unfortunately an experience all Windows users are accustomed to — things don’t “just work.”
Security Isn’t Automatically Better
Computerworld’s Steven Vaughan-Nichols stands firm that Windows 7 won’t change anything from a security perspective: “Windows 7 still has all the security of a drunken teenager in a sports car,” he wrote. “Millions of lazy Windows users are the reason why the internet is a mess. If you already do all the right things to keep XP running safely, you’re not going to get any safer by buying Windows 7.”
Good point. Because Windows 7 is still Windows, you’re again the primary target of attack for hackers and virus coders. Therefore, it’s up to you to protect yourself with anti-virus software and running update patches to keep the OS as secure as possible. (Compare this experience to Mac OS X Leopard, for which many don’t even run anti-virus software, because it’s more secure out-of-the-box compared to Windows.) Though Windows 7 does deliver some security enhancements, such as data encryption for thumb drives, and a feature for IT administrators to control which applications can run on a corporate network, these are not general security improvements that change much for the overall user experience.
Built-In Support for Egregious Hardware-Based DRM
Paranoid XP users won’t wish to upgrade to Windows 7 for the same reason they didn’t switch to Vista: Like Vista, Windows 7 includes support for digital rights management technologies that could potentially regulate how you use your media. Though some alarmists have called Microsoft’s DRM “draconian,” the implemented DRM hasn’t proved to bear significant consequences yet.
Ars Technica provides a thorough explanation of the DRM in question. In short, the technologies called Protected Video Path (PVP) and Protected User Mode Audio (PUMA) provide secure playback of video and audio media, respectively. “Little or no media actually demands the use of the protected paths, so on most users’ systems, Windows never invokes them,” wrote Ars Technica’s Peter Bright. “Play back unprotected media on a Vista machine, and the DRM subsystems simply don’t get used.”
Still, there are going to be people cringing in fear that one day PUMA and PVP will screw them over. And for that reason they’ll be sticking with XP — or a totally open OS like Linux.
Snow Leopard Is Almost Here
Apple’s next-generation Snow Leopard is arriving September — a month before Windows 7. Apple is promising its OS will deliver on many of the improvements Microsoft highlights in Windows 7 — 64-bit addressing, improved efficiency with task management on multiple processors, and others. It’s undetermined which OS is better, but from my own perspective as a long-time Mac user, I will say I already prefer the current Mac OS X Leopard to Windows 7. If you’re looking (or willing) to switch to a radically different OS, then OS X Snow Leopard is an option to consider before committing to Windows 7.
Conclusion
Do the cons outweigh the pros? That probably depends on how committed you already are to Windows. If you’re currently using Windows Vista, the upgrade to Windows 7 is a no-brainer. Most of those currently using Windows XP should also upgrade, to take advantage of Windows 7’s usability, enhanced device support, and other features. But if you’re currently using a Linux distribution or a version of Mac OS X, Windows 7 isn’t going to offer much to get you to switch.
7 Things You Should Know About Upgrading to Windows 7
Thursday is a big day for Windows users. Microsoft is finally making Windows 7 publicly available, and the number of pre-orders for the operating system on Amazon.com has already surpassed orders for Harry Potter in the U.K.
Not bad for an operating system that costs $120 and doesn’t even have any magic wands or dragons in it.
That’s a good indicator that a lot of people are upgrading, and we’re sure there will be even more that follow after consumers spread the word about the vast improvements in Windows 7 over its predecessors. Here’s a simple guideline of what you should know to ensure your upgrade process is smooth — from purchase to install.
1. You should get this upgrade
We’ve written about Windows 7’s strong points as well as its weaker points. On balance, we’re confident saying this is the best Microsoft operating system yet. If you’re running any earlier version of Windows, you’ll almost certainly want to upgrade — and you should feel no hesitation about buying new computers preloaded with Windows 7.
2. But you’ll have to pay for it
Apple offers an upgrade to its latest operating system, Snow Leopard, for $30 — and you can even take advantage of it if you don’t have the previous version, Leopard. Not so with Microsoft: You’ll need to pay $120 for the upgrade — or even more, depending on which version you get. (Unless you’re a smart shopper and can find a discounted price. See tips 6 and 7 below for details on which version to buy and how to find discounts.) As with previous versions of Windows, Microsoft has created a bewildering array of variations.
3. Double-check compatibility with your hardware
Paranoid about losing access to some of your third-party accessories and software after upgrading? You should be, at least a little bit. Microsoft claims Windows 7 will work smoothly with most third-party gadgets and software, but to be on the safe side, you should check out the Windows 7 Upgrade Advisor. The tool automatically scans your system and provides a report of any potential issues, as well as steps to resolve them.
4. Scout for computers shipping with Windows 7
If you’ve been shopping for a new computer — but waiting for Windows 7 to come out first — there’s a Microsoft tool to help search for new computers that ship with Windows 7. It’s called PC Scout, and it searches for computers based on your preferences. As of this writing, the results don’t bring up Windows 7 systems (since Windows 7 isn’t officially released yet), but the website clarifies that all the computers listed in the database are eligible for a Windows 7 upgrade. That means if you purchase one of those computers today, all you have to pay is $10 for shipping, and you get the Windows 7 upgrade free. By the time Windows 7 ships, the PC Scout should be showing results for computers that include Windows 7.
Amazon customers shopping for Windows 7 computers: There’s a web page just for you. Amazon breaks down a list of netbooks, notebooks and desktops shipping with Windows 7, so definitely check those out.
5. Upgrading from XP? Back up your data, wipe and migrate
Windows XP users cannot do a straight upgrade; they’ll have to back up their files, format their hard drive and perform a clean install. After your fresh copy of Windows 7 is on your computer, Microsoft offers a tool called Easy Transfer to migrate your files.
(If you’re a Vista user, you’ll be able to upgrade without doing a clean install — though fresh installations are generally recommended for optimal performance anyway whenever you switch to a new operating system.)
6. Know what you want
Disregard the awful, intimidating Windows 7 upgrade chart when you’re picking a version to buy. Choosing the right version really isn’t as complicated as Microsoft has made it sound in the past. Consumers: The vast majority of you should go with Windows 7 Home Premium. Business users: Most of you will want to go with Windows 7 Professional. (There’s a Windows 7 Ultimate edition, but that’s aimed at a very niche audience of ultra geeks who want to do everything they could possibly imagine doing with their computers.) Again, if you want to be safe, use the Upgrade Advisor to check your hardware and software compatibility.
7. Look for limited-time discounts
If you’re buying Windows 7 while it’s brand new, you shouldn’t be paying the full price. Microsoft and its partners are holding a weeklong sale called “7 Days of Windows 7.” Companies offering Windows 7 discounts with Microsoft include Best Buy, Dell and Acer. You can sign up to hear about daily offers on Windows.com. Also, you can check discount-aggregation sites such as PriceGrabber.com or Froogle.com to find the cheapest Windows 7 deals.
Not bad for an operating system that costs $120 and doesn’t even have any magic wands or dragons in it.
That’s a good indicator that a lot of people are upgrading, and we’re sure there will be even more that follow after consumers spread the word about the vast improvements in Windows 7 over its predecessors. Here’s a simple guideline of what you should know to ensure your upgrade process is smooth — from purchase to install.
1. You should get this upgrade
We’ve written about Windows 7’s strong points as well as its weaker points. On balance, we’re confident saying this is the best Microsoft operating system yet. If you’re running any earlier version of Windows, you’ll almost certainly want to upgrade — and you should feel no hesitation about buying new computers preloaded with Windows 7.
2. But you’ll have to pay for it
Apple offers an upgrade to its latest operating system, Snow Leopard, for $30 — and you can even take advantage of it if you don’t have the previous version, Leopard. Not so with Microsoft: You’ll need to pay $120 for the upgrade — or even more, depending on which version you get. (Unless you’re a smart shopper and can find a discounted price. See tips 6 and 7 below for details on which version to buy and how to find discounts.) As with previous versions of Windows, Microsoft has created a bewildering array of variations.
3. Double-check compatibility with your hardware
Paranoid about losing access to some of your third-party accessories and software after upgrading? You should be, at least a little bit. Microsoft claims Windows 7 will work smoothly with most third-party gadgets and software, but to be on the safe side, you should check out the Windows 7 Upgrade Advisor. The tool automatically scans your system and provides a report of any potential issues, as well as steps to resolve them.
4. Scout for computers shipping with Windows 7
If you’ve been shopping for a new computer — but waiting for Windows 7 to come out first — there’s a Microsoft tool to help search for new computers that ship with Windows 7. It’s called PC Scout, and it searches for computers based on your preferences. As of this writing, the results don’t bring up Windows 7 systems (since Windows 7 isn’t officially released yet), but the website clarifies that all the computers listed in the database are eligible for a Windows 7 upgrade. That means if you purchase one of those computers today, all you have to pay is $10 for shipping, and you get the Windows 7 upgrade free. By the time Windows 7 ships, the PC Scout should be showing results for computers that include Windows 7.
Amazon customers shopping for Windows 7 computers: There’s a web page just for you. Amazon breaks down a list of netbooks, notebooks and desktops shipping with Windows 7, so definitely check those out.
5. Upgrading from XP? Back up your data, wipe and migrate
Windows XP users cannot do a straight upgrade; they’ll have to back up their files, format their hard drive and perform a clean install. After your fresh copy of Windows 7 is on your computer, Microsoft offers a tool called Easy Transfer to migrate your files.
(If you’re a Vista user, you’ll be able to upgrade without doing a clean install — though fresh installations are generally recommended for optimal performance anyway whenever you switch to a new operating system.)
6. Know what you want
Disregard the awful, intimidating Windows 7 upgrade chart when you’re picking a version to buy. Choosing the right version really isn’t as complicated as Microsoft has made it sound in the past. Consumers: The vast majority of you should go with Windows 7 Home Premium. Business users: Most of you will want to go with Windows 7 Professional. (There’s a Windows 7 Ultimate edition, but that’s aimed at a very niche audience of ultra geeks who want to do everything they could possibly imagine doing with their computers.) Again, if you want to be safe, use the Upgrade Advisor to check your hardware and software compatibility.
7. Look for limited-time discounts
If you’re buying Windows 7 while it’s brand new, you shouldn’t be paying the full price. Microsoft and its partners are holding a weeklong sale called “7 Days of Windows 7.” Companies offering Windows 7 discounts with Microsoft include Best Buy, Dell and Acer. You can sign up to hear about daily offers on Windows.com. Also, you can check discount-aggregation sites such as PriceGrabber.com or Froogle.com to find the cheapest Windows 7 deals.
Friday, September 25, 2009
Sistema operativo
Un sistema operativo es un software de sistema, es decir, un conjunto de programas de computación destinados a realizar muchas tareas entre las que destaca la administración de los dispositivos externos como mouse, teclado, cámara web etc.
En otras palabras el sistema operativo de una computadora es la interface o el modo de comunicación, entre la persona y la computadora, sin el sistema operativo sería muy difícil o casi imposible usar nuestro sistema de computación. Imaginémonos que el sistema operativo es lo que podemos ver adentro de un carro cuando nos subimos a manejar, el volante, acelerador, frenos, medidor de velocidad, temperatura, etc, sin esta interface no podríamos manejar un carro.
Los sistemas operativos más comunes son:
Microsoft Windows. Los más actuales son XP, Vista y el más nuevo Windows 7
Macintosh-Apple computes Mac OX 8, Mac OX 9 and Mac OS X
Linux de open source
gOS de open source
Existen muchos mas sistemas operativos que no son tan usados como los que mencionamos.
Google está planeando sacar un sistema operativo gratis llamado Google Chrome y estará listo, en una versión preliminar para netbooks (pequeñas notebooks dedicadas a la Web) a fines de este año.
En otras palabras el sistema operativo de una computadora es la interface o el modo de comunicación, entre la persona y la computadora, sin el sistema operativo sería muy difícil o casi imposible usar nuestro sistema de computación. Imaginémonos que el sistema operativo es lo que podemos ver adentro de un carro cuando nos subimos a manejar, el volante, acelerador, frenos, medidor de velocidad, temperatura, etc, sin esta interface no podríamos manejar un carro.
Los sistemas operativos más comunes son:
Microsoft Windows. Los más actuales son XP, Vista y el más nuevo Windows 7
Macintosh-Apple computes Mac OX 8, Mac OX 9 and Mac OS X
Linux de open source
gOS de open source
Existen muchos mas sistemas operativos que no son tan usados como los que mencionamos.
Google está planeando sacar un sistema operativo gratis llamado Google Chrome y estará listo, en una versión preliminar para netbooks (pequeñas notebooks dedicadas a la Web) a fines de este año.
Wednesday, August 26, 2009
¿Cuáles son las herramientas de código abierto?
Ver esta definición de Open Source: http://opensource.org/docs/osd
En términos generales, "Open Source" se refiere a un movimiento donde el software, tanto el código interno y el producto final, son gratuitas y abiertas a todo el mundo. ¿Cómo es esto de interés para su computadora? Después de más de 10 años de evolución de las prácticas y normas, programas informáticos de código abierto se ha convertido en una fuerza importante en la industria de software. Todo, desde el software que compite con Microsoft Windows y Microsoft Office, para los navegadores de Internet, herramientas de privacidad, herramientas de seguridad, herramientas de acceso remoto, herramientas administrativas, los editores de audio, herramientas de diseño gráfico, base de datos y tecnologías de código abierto se ha tocado casi todos los aspectos del software desarrollo.
B. ¿Qué tipo de software de código abierto están disponibles y dónde puedo encontrarlos?
El universo de las herramientas de código abierto es amplia, pero aquí hay algunas muy potente, Open Source y / o herramientas libres que puede utilizar para mejorar la eficiencia de su computadora:
• AVG Anti-virus, anti-spyware y anti-rootkit
Sitio: http://free.grisoft.com/
Resumen: Protege tu computadora de virus y spyware con una suite de productos
En términos generales, "Open Source" se refiere a un movimiento donde el software, tanto el código interno y el producto final, son gratuitas y abiertas a todo el mundo. ¿Cómo es esto de interés para su computadora? Después de más de 10 años de evolución de las prácticas y normas, programas informáticos de código abierto se ha convertido en una fuerza importante en la industria de software. Todo, desde el software que compite con Microsoft Windows y Microsoft Office, para los navegadores de Internet, herramientas de privacidad, herramientas de seguridad, herramientas de acceso remoto, herramientas administrativas, los editores de audio, herramientas de diseño gráfico, base de datos y tecnologías de código abierto se ha tocado casi todos los aspectos del software desarrollo.
B. ¿Qué tipo de software de código abierto están disponibles y dónde puedo encontrarlos?
El universo de las herramientas de código abierto es amplia, pero aquí hay algunas muy potente, Open Source y / o herramientas libres que puede utilizar para mejorar la eficiencia de su computadora:
• AVG Anti-virus, anti-spyware y anti-rootkit
Sitio: http://free.grisoft.com/
Resumen: Protege tu computadora de virus y spyware con una suite de productos
Computers
Computers are magnificent tools for the realization of our dreams, but no machine can replace the human spark of spirit, compassion, love, and understanding.
Wednesday, August 19, 2009
¿Porque mi computadora está funcionando lenta? ¿Qué medidas puedo hacer para arreglarla?
Incluso si usted es muy cuidadoso acerca de cómo usted utiliza su computadora y nunca descarga material cuestionable, con el tiempo es inevitable que en su sistema se acumulan las entradas del Registro no deseado, errores, desorden y suciedad.
Las causas más comunes son la instalación y desinstalación del software, los juegos en línea. Si bien muchos errores pasan desapercibidos, existen otros que nos van a causar problemas. Otras cusa por la cual nuestra computadora se siente muy despacio o se frisa es por Infecciones, virus, adware, spyware etc. Poca memoria RAM La unidad del disco duro tiene poco espacio disponible en el disco.
Datos Corruptos
La computadora se sobrecalienta.
Sistema operativo corrupto.
Hardware dañado.
Herramientas para mantener un equipo de computación saludable.
Herramienta de privacidad: Ccleaner limpia las galletas (Cookies) y archivos temporales (temporary files) que se quedan en el disco duro cada vez que navega en el internet y también limpia las registry keys que se queda en nuestra computadora cada vez que instalamos, actualizamos y quitamos software.
Antivirus, preferencia AVG o Avira
Anti spyware: Spybot excelente herramienta para limpiar de adware y spyware.
Abrir el internet con un navegador (browser) alternativo a internet Explorer, nosotros siempre recomendamos que usen firefox para navegar en el internet.
Instalar lo máxima de memoria RAM que su computadora soporta.
Y por ultimo si el problema es físico (hardware) tiene que llevarlo con un técnico para que le de un diagnostico.
Nota: las herramientas que menciono en este artículo son herramientas que nosotros tenemos usando por mucho tiempo, son gratis y muy efectivas, existen muchas otras herramientas que también hemos usados en el pasado y que no son tan efectivas.
Las causas más comunes son la instalación y desinstalación del software, los juegos en línea. Si bien muchos errores pasan desapercibidos, existen otros que nos van a causar problemas. Otras cusa por la cual nuestra computadora se siente muy despacio o se frisa es por Infecciones, virus, adware, spyware etc. Poca memoria RAM La unidad del disco duro tiene poco espacio disponible en el disco.
Datos Corruptos
La computadora se sobrecalienta.
Sistema operativo corrupto.
Hardware dañado.
Herramientas para mantener un equipo de computación saludable.
Herramienta de privacidad: Ccleaner limpia las galletas (Cookies) y archivos temporales (temporary files) que se quedan en el disco duro cada vez que navega en el internet y también limpia las registry keys que se queda en nuestra computadora cada vez que instalamos, actualizamos y quitamos software.
Antivirus, preferencia AVG o Avira
Anti spyware: Spybot excelente herramienta para limpiar de adware y spyware.
Abrir el internet con un navegador (browser) alternativo a internet Explorer, nosotros siempre recomendamos que usen firefox para navegar en el internet.
Instalar lo máxima de memoria RAM que su computadora soporta.
Y por ultimo si el problema es físico (hardware) tiene que llevarlo con un técnico para que le de un diagnostico.
Nota: las herramientas que menciono en este artículo son herramientas que nosotros tenemos usando por mucho tiempo, son gratis y muy efectivas, existen muchas otras herramientas que también hemos usados en el pasado y que no son tan efectivas.
Tuesday, August 18, 2009
¿Qué son las infecciones, virus y gusanos de computadoras?
Pensemos en un virus cibernético de la misma manera que una infección o virus biológico afecta nuestro cuerpo, son partículas infecciosas que vive dentro de nuestra computadora y no la deja funcionar correctamente o como cuando nosotros estamos enfermos, no podemos hacer nuestras labores diarias de la misma manera como cuando estamos saludables.
Algunas infecciones pueden ser curables con un buen antivirus (vacunas) y otras herramientas que voy a mencionar más adelante, pero muchas de las infecciones son tan fuertes que hacen que a nuestra computadora le de neumonía y tengamos que ir corriendo al cuarto de emergencia para que sea tratada por un profesional.
Gusanos
Estos programas se ocupan principalmente de hacer copias de sí mismos haciendo uso de las facilidades de comunicaciones del equipo (conexiones de red, correo electrónico,...). La mayoría no tiene efectos directamente destructivos, pero su crecimiento exponencial puede colapsar por saturación las redes en las que se infiltran. A diferencia de los virus de fichero, no necesitan infectar ni dañar otros archivos.
¿Cómo prevenir que nuestra computadora se contamine?
1.- Utiliza un buen antivirus y actualízalo diariamente.
Existen muchísimos programas de antivirus en el mercado y algunos de ellos son gratis y tan buenos o mejores que los que se compran, como AVG ANTIVIRUS y AVIRA ANTIVIR. (Gratis para uso personal)
2.- Asegúrate de que tu antivirus esté siempre activo.
Un antivirus está activo cuando dispone de una protección permanente capaz de vigilar constantemente todas las operaciones realizadas en el ordenador.
Existen dos maneras de comprobar que esta protección permanente esté activada; a través de un icono fijo en la barra de tareas, junto a la información horaria, o en la propia configuración del programa antivirus.
Estar protegido contra los virus requiere una protección permanente, tanto de archivos como de correo electrónico.
3.- Evita descargar programas de lugares no seguros en Internet.
Tengan mucho cuidado al Bajar archivos del internet cuando no reconoces la procedencia, música, películas, lo que bajas cuando utilizas programas (peer to peer) computadora a computadora.
¿Cuáles son las señales de que nuestra computadora podría estar contaminada? Si su la computadora actúa muy despacio, si tienen muchas ventanas de publicidad (pop ups) cuando quiere ir a un sitio en el internet y lo manda a otro sitio o dirección.
Algunas infecciones pueden ser curables con un buen antivirus (vacunas) y otras herramientas que voy a mencionar más adelante, pero muchas de las infecciones son tan fuertes que hacen que a nuestra computadora le de neumonía y tengamos que ir corriendo al cuarto de emergencia para que sea tratada por un profesional.
Gusanos
Estos programas se ocupan principalmente de hacer copias de sí mismos haciendo uso de las facilidades de comunicaciones del equipo (conexiones de red, correo electrónico,...). La mayoría no tiene efectos directamente destructivos, pero su crecimiento exponencial puede colapsar por saturación las redes en las que se infiltran. A diferencia de los virus de fichero, no necesitan infectar ni dañar otros archivos.
¿Cómo prevenir que nuestra computadora se contamine?
1.- Utiliza un buen antivirus y actualízalo diariamente.
Existen muchísimos programas de antivirus en el mercado y algunos de ellos son gratis y tan buenos o mejores que los que se compran, como AVG ANTIVIRUS y AVIRA ANTIVIR. (Gratis para uso personal)
2.- Asegúrate de que tu antivirus esté siempre activo.
Un antivirus está activo cuando dispone de una protección permanente capaz de vigilar constantemente todas las operaciones realizadas en el ordenador.
Existen dos maneras de comprobar que esta protección permanente esté activada; a través de un icono fijo en la barra de tareas, junto a la información horaria, o en la propia configuración del programa antivirus.
Estar protegido contra los virus requiere una protección permanente, tanto de archivos como de correo electrónico.
3.- Evita descargar programas de lugares no seguros en Internet.
Tengan mucho cuidado al Bajar archivos del internet cuando no reconoces la procedencia, música, películas, lo que bajas cuando utilizas programas (peer to peer) computadora a computadora.
¿Cuáles son las señales de que nuestra computadora podría estar contaminada? Si su la computadora actúa muy despacio, si tienen muchas ventanas de publicidad (pop ups) cuando quiere ir a un sitio en el internet y lo manda a otro sitio o dirección.
Wednesday, August 12, 2009
What is a Network?
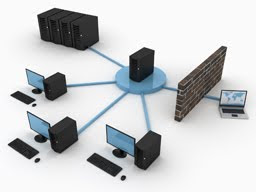
A network is a collection of computers and other devices connected to each other for the purpose of sharing information and resources. Common network elements include:
• Printers – one printer can be shared across several users
• File servers – a common repository of critical information, usually in the form of Word and Excel documents that can be shared across your company. Access can be controlled with security policies
• Application servers – Some programs do not run from the desktop, but rather, are accessed from a central server. SugarCRM is an example of a web-based application that can reside on an application server.
• Database servers – a common repository of business information, such as a client database, invoicing, purchasing, and reporting. Newer versions of QuickBooks allow for a database server configuration.
• E-mail servers – a server can be configured on your network to support e-mail access for your entire organization. Given the administrative overhead of providing > 99% uptime, spam reduction, and quotas for each user’s inbox, many smaller companies opt to use an external host for e-mail services. However, many larger companies do benefit from managing this internally.
• Shared Internet access – one Internet connection can be shared across your company without a noticeable reduction in performance for most basic applications
• Smart phones and other hand-held devices – Synchronization of calendars, contact information, and even Internet access and business applications can be accessed with many current hand-held devices
Properly configured and maintained, a network can help you streamline your business processes, increase productivity, and maximize the return on your investment in technology. A poorly implemented and/or a poorly maintained network can have exactly the opposite result.
Password management
Do you use your kids' names? Your pet's? Your favorite color? We all use some dumb passwords that are too easy to guess.
Worse, we use the same ones for lots of Web sites. So if one site gets compromised, or an employee there is dishonest, someone could start trying out that password on other sites where you have accounts, like Amazon or PayPal, and you've got trouble.
• KeePass
Site: http://keepass.info/
Summary: “KeePass is a free/open-source password manager or safe which helps you to manage your passwords in a secure way. You can put all your passwords in one database, which is locked with one master key or a key-disk. So you only have to remember one single master password or insert the key-disk to unlock the whole database. The databases are encrypted using the best and most secure encryption algorithms currently known (AES and Twofish).”
Worse, we use the same ones for lots of Web sites. So if one site gets compromised, or an employee there is dishonest, someone could start trying out that password on other sites where you have accounts, like Amazon or PayPal, and you've got trouble.
• KeePass
Site: http://keepass.info/
Summary: “KeePass is a free/open-source password manager or safe which helps you to manage your passwords in a secure way. You can put all your passwords in one database, which is locked with one master key or a key-disk. So you only have to remember one single master password or insert the key-disk to unlock the whole database. The databases are encrypted using the best and most secure encryption algorithms currently known (AES and Twofish).”
General Motors, prueba la venta de automoviles nuevos atravez de e-bay
General Motors Co Inc y eBay están poniendo en marcha un programa de pruebas en California que permitirá a los consumidores a negociar con los distribuidores y comprar vehículos nuevos en línea, las empresas dijeron el lunes.
El sitio web de compras de coches - gm.ebay.com - marca una salida del camino los vehículos nuevos han sido tradicionalmente vendidos en los Estados Unidos y está destinada a ayudar a recuperar GM perdió cuota de mercado un mes después de que surgió de la quiebra.
El sitio web permite a los consumidores a comparar precios y modelos a través de los concesionarios participantes, negociar precios, y financiación de pago. Los consumidores pueden pagar de acuerdo a la publicidad de precios o indicar el precio que están dispuestos a pagar y pueden negociar con el distribuidor en línea para el vehículo.
Más de 20.000 nuevos Chevrolet, Buick, GMC y Pontiac vehículos será incluido inicialmente en el sitio.
El sitio web de compras de coches - gm.ebay.com - marca una salida del camino los vehículos nuevos han sido tradicionalmente vendidos en los Estados Unidos y está destinada a ayudar a recuperar GM perdió cuota de mercado un mes después de que surgió de la quiebra.
El sitio web permite a los consumidores a comparar precios y modelos a través de los concesionarios participantes, negociar precios, y financiación de pago. Los consumidores pueden pagar de acuerdo a la publicidad de precios o indicar el precio que están dispuestos a pagar y pueden negociar con el distribuidor en línea para el vehículo.
Más de 20.000 nuevos Chevrolet, Buick, GMC y Pontiac vehículos será incluido inicialmente en el sitio.
Tuesday, August 11, 2009
Windows 7 Upgrades
Need to buy 100 PCs today? Microsoft says businesses can only have free upgrades to Windows 7 on 25 of those machines. In this opinion piece, CIO.com's Shane O'Neill says businesses should just say no to this "deal" — and pressure PC makers to help out.
On one hand, Microsoft may seem generous for allowing companies to upgrade 25 purchased machines to Windows 7 for free between now and the Oct. 22 planned ship date for the new OS. After all, that's five times the amount of free licenses that it offered companies for Vista upgrades three years ago.
Slideshow: Windows 7 in Pictures: 10 Cool Desktop Features
But that was a different time, a better economy. These days, the 25 PCs gesture is not enough.
It's not enough, because Vista was a debacle for early adopters. Vista didn't deliver on its promises and caused businesses stress and anxiety, forcing many to make do with the more solid, albeit aging, Windows XP.
Although I think there's too many rants out there on the Web now about how all the long-suffering Vista users should get Windows 7 for free forever, heck, with a new car thrown in, I do think businesses are owed better and cheaper access to Windows 7 because of Vista's failure in the enterprise.
I also think the 25-PC limit should not be tolerated because of our crippling economic downturn and because it's a sneaky tactic by Microsoft to get companies to pay up for a Software Assurance agreement, which costs $100 - $150 per machine for unlimited upgrades at no additional cost for three years.
Microsoft kept the 25-PC limit in very fine print when it announced its free Windows 7 Upgrade Option plan last week.
Only the smallest of companies will not be affected by the PC limit; companies that need to buy, say 100 PCs right now, will have to pay for Windows twice (Vista initially and then the license for Windows 7 when it releases) for 75 of them. As PCWorld's David Coursey asks: Why pay now and pay later?
What are companies' other options? You can wait until Oct. 22 to buy new machines with Windows 7 pre-loaded, though being forced to wait to make needed purchase in a recession is lame. Companies could spend extra money on a Software Assurance agreement and then buy however many machines they want and get free upgrades (that's what Microsoft wants).
Or, companies could fight the system, using PC makers as allies (what Microsoft most definitely does not want).
In a report titled "Enterprises Should Demand Windows Upgrade Option", Gartner research director Michael Silver slams Microsoft's 25-PC Windows 7 upgrade limit, emphasizing that businesses still have the right to bypass Microsoft and negotiate with PC makers that have leverage in this area.
On one hand, Microsoft may seem generous for allowing companies to upgrade 25 purchased machines to Windows 7 for free between now and the Oct. 22 planned ship date for the new OS. After all, that's five times the amount of free licenses that it offered companies for Vista upgrades three years ago.
Slideshow: Windows 7 in Pictures: 10 Cool Desktop Features
But that was a different time, a better economy. These days, the 25 PCs gesture is not enough.
It's not enough, because Vista was a debacle for early adopters. Vista didn't deliver on its promises and caused businesses stress and anxiety, forcing many to make do with the more solid, albeit aging, Windows XP.
Although I think there's too many rants out there on the Web now about how all the long-suffering Vista users should get Windows 7 for free forever, heck, with a new car thrown in, I do think businesses are owed better and cheaper access to Windows 7 because of Vista's failure in the enterprise.
I also think the 25-PC limit should not be tolerated because of our crippling economic downturn and because it's a sneaky tactic by Microsoft to get companies to pay up for a Software Assurance agreement, which costs $100 - $150 per machine for unlimited upgrades at no additional cost for three years.
Microsoft kept the 25-PC limit in very fine print when it announced its free Windows 7 Upgrade Option plan last week.
Only the smallest of companies will not be affected by the PC limit; companies that need to buy, say 100 PCs right now, will have to pay for Windows twice (Vista initially and then the license for Windows 7 when it releases) for 75 of them. As PCWorld's David Coursey asks: Why pay now and pay later?
What are companies' other options? You can wait until Oct. 22 to buy new machines with Windows 7 pre-loaded, though being forced to wait to make needed purchase in a recession is lame. Companies could spend extra money on a Software Assurance agreement and then buy however many machines they want and get free upgrades (that's what Microsoft wants).
Or, companies could fight the system, using PC makers as allies (what Microsoft most definitely does not want).
In a report titled "Enterprises Should Demand Windows Upgrade Option", Gartner research director Michael Silver slams Microsoft's 25-PC Windows 7 upgrade limit, emphasizing that businesses still have the right to bypass Microsoft and negotiate with PC makers that have leverage in this area.
¿Cómo escoger una computadora?
Las preguntas que nos debemos contestar son:
¿Cuál es tu presupuesto? Y en base a lo que quiera gastar, compra la computadora con el máximo de memoria (RAM), el más rápido CPU y el disco duro (Hard drive) más grande, en ese orden, por ejemplo si solo puedes aumentar la memoria es mejor tener más RAM con un CPU de 1.60 GHz a un CPU de 2.2 GHz y poca memoria, para XP se recomienda mínimo 512MG of RAM y para Vista 1GB, entre mas memoria tengas en tu PC mejor va a funcionar tu computadora. Y por último el disco duro.
¿Para que la vas a usar? Si la vas usar para uso básico, como navegar en le internet, correo electrónico, y hacer documentos con programas de office, no necesitas una computadora muy poderosa. Si tu objetivo es para juegos con gráficos muy intensos o video editing, es recomendable comprar con el máximo de memoria RAM, rápido CPU y un disco duro con una capacidad de almacenamiento grande.
¿Y donde la vas a usar? si eres una persona que viajas mucho, necesitas mover tu computadora frecuentemente o usas el tren una laptop o netbook es lo más recomendable.
Actualmente los precios de una computadora nueva comienzan desde $299 para una computadora de escritorio y $399 para una computadora portátil.
Información General:
La memoria de acceso aleatorio, (en inglés: Random Access Memory cuyo acrónimo es RAM) es la memoria desde donde el procesador recibe las instrucciones y guarda los resultados. En otras palabras es una memoria volátil que se usa mientras tu computadora está encendida.
La unidad central de procesamiento, o CPU (por las siglas en inglés Central Processing Unit), o, simplemente, el procesador, es el componente en una computadora digital que interpreta las instrucciones y procesa los datos contenidos en los programas de la computadora. Es el cerebro de la computadora actualmente vienen dou core, quatro core. Físicamente un CPU pero actúa como dos o cuatro.
Disco duro o disco rígido (en inglés hard disk drive) es un dispositivo de almacenamiento no volátil, que conserva la información aun con la pérdida de energía. Es donde todos los programas están almacenados, incluyendo el sistema operativo.
Hardware: si lo traducimos a español es materia dura, en términos de computación es lo que vemos y podemos tocar.
Software: Materia blanda es lo abstracto, lo que no vemos y no tocamos, en nuestra computadora es el software.
¿Cuál es tu presupuesto? Y en base a lo que quiera gastar, compra la computadora con el máximo de memoria (RAM), el más rápido CPU y el disco duro (Hard drive) más grande, en ese orden, por ejemplo si solo puedes aumentar la memoria es mejor tener más RAM con un CPU de 1.60 GHz a un CPU de 2.2 GHz y poca memoria, para XP se recomienda mínimo 512MG of RAM y para Vista 1GB, entre mas memoria tengas en tu PC mejor va a funcionar tu computadora. Y por último el disco duro.
¿Para que la vas a usar? Si la vas usar para uso básico, como navegar en le internet, correo electrónico, y hacer documentos con programas de office, no necesitas una computadora muy poderosa. Si tu objetivo es para juegos con gráficos muy intensos o video editing, es recomendable comprar con el máximo de memoria RAM, rápido CPU y un disco duro con una capacidad de almacenamiento grande.
¿Y donde la vas a usar? si eres una persona que viajas mucho, necesitas mover tu computadora frecuentemente o usas el tren una laptop o netbook es lo más recomendable.
Actualmente los precios de una computadora nueva comienzan desde $299 para una computadora de escritorio y $399 para una computadora portátil.
Información General:
La memoria de acceso aleatorio, (en inglés: Random Access Memory cuyo acrónimo es RAM) es la memoria desde donde el procesador recibe las instrucciones y guarda los resultados. En otras palabras es una memoria volátil que se usa mientras tu computadora está encendida.
La unidad central de procesamiento, o CPU (por las siglas en inglés Central Processing Unit), o, simplemente, el procesador, es el componente en una computadora digital que interpreta las instrucciones y procesa los datos contenidos en los programas de la computadora. Es el cerebro de la computadora actualmente vienen dou core, quatro core. Físicamente un CPU pero actúa como dos o cuatro.
Disco duro o disco rígido (en inglés hard disk drive) es un dispositivo de almacenamiento no volátil, que conserva la información aun con la pérdida de energía. Es donde todos los programas están almacenados, incluyendo el sistema operativo.
Hardware: si lo traducimos a español es materia dura, en términos de computación es lo que vemos y podemos tocar.
Software: Materia blanda es lo abstracto, lo que no vemos y no tocamos, en nuestra computadora es el software.
Microsoft Surprises with Free Office Apps
The surprises from Microsoft just keep coming. The most interesting aspect of this week's Microsoft Office 2010 announcements was that the online web version of Office 2010 apps will be free. That's free from three perspectives; free to users with a Windows Live account, free Microsoft hosted Office Web apps, and free customer hosted Office Web apps for Microsoft Software Assurance enterprise customers. Free, free, free. Only SMBs who opt for Office 2010 web apps instead of buying regular Office software will have to pay extra, some estimate at a comparable (to Google Apps Premier Edition) $50 price. It may not be $50 but I'll bet that's not too far off.
Yes, Office 2010 web apps will be lesser functional cousins of the full software versions, but there's a good chance many will be able to make use of the web versions of Office, otherwise why would Microsoft bother offering it for free to Software Assurance customers, and in a paid version targeted at SMBs? I expect one of the biggest pluses of Office web apps is their integration with SharePoint 2010, giving the apps a full backend data store to organize and access documents, and an integrated experience via a SharePoint portal. Office web apps gives SharePoint an extra leg up on the competition, by embedding a much richer set of apps into the portal software, vs. the standard web page editing form nearly all other portal and wiki technologies rely upon.
Microsoft's strategy here is to offer the best of all worlds; rich installed apps and web versions, standalone office apps and Office integrated into SharePoint, and a pubic Windows Live version offering, Microsoft hosted offering or customer internally hosted option. Google's only giving users one option; Google web apps are only hosted on Google's servers, and there's nothing near an equivalent to SharePoint 2010 and Workspace 2010 (formerly Groove) from Google. Other than being the "anti-Microsoft" option, Google looks pretty limited in comparison. Microsoft Office web apps may also eat into the uses of open source Open Office software, since
Microsoft's web apps will work under Firefox and Safari, in addition to IE. (Notice not Google Chrome support.)
I stand by what I said in last week's post, Google's Still No Threat To Microsoft even more so.
Las sorpresas de Microsoft sólo siguen viniendo. El aspecto más interesante de esta semana los anuncios de Microsoft Office 2010 es que la versión online de aplicaciones de Office 2010 será gratuita. Eso es libre desde tres perspectivas; la libertad de los usuarios con una cuenta de Windows Live, gratis Microsoft Office Web alojada aplicaciones, los clientes alojados y libre de aplicaciones de Office Web de Microsoft Software Assurance para clientes empresariales. Gratis, libre, gratis. Sólo pymes que opten por la Oficina 2010 aplicaciones web en lugar de comprar software de oficina regulares tendrán que pagar más, algunos en una estimación comparable (a Google Apps edición premier) $ 50 el precio. Puede que no sea $ 50, pero yo apuesto a que no es demasiado lejos.
Yes, Office 2010 web apps will be lesser functional cousins of the full software versions, but there's a good chance many will be able to make use of the web versions of Office, otherwise why would Microsoft bother offering it for free to Software Assurance customers, and in a paid version targeted at SMBs? I expect one of the biggest pluses of Office web apps is their integration with SharePoint 2010, giving the apps a full backend data store to organize and access documents, and an integrated experience via a SharePoint portal. Office web apps gives SharePoint an extra leg up on the competition, by embedding a much richer set of apps into the portal software, vs. the standard web page editing form nearly all other portal and wiki technologies rely upon.
Microsoft's strategy here is to offer the best of all worlds; rich installed apps and web versions, standalone office apps and Office integrated into SharePoint, and a pubic Windows Live version offering, Microsoft hosted offering or customer internally hosted option. Google's only giving users one option; Google web apps are only hosted on Google's servers, and there's nothing near an equivalent to SharePoint 2010 and Workspace 2010 (formerly Groove) from Google. Other than being the "anti-Microsoft" option, Google looks pretty limited in comparison. Microsoft Office web apps may also eat into the uses of open source Open Office software, since
Microsoft's web apps will work under Firefox and Safari, in addition to IE. (Notice not Google Chrome support.)
I stand by what I said in last week's post, Google's Still No Threat To Microsoft even more so.
Las sorpresas de Microsoft sólo siguen viniendo. El aspecto más interesante de esta semana los anuncios de Microsoft Office 2010 es que la versión online de aplicaciones de Office 2010 será gratuita. Eso es libre desde tres perspectivas; la libertad de los usuarios con una cuenta de Windows Live, gratis Microsoft Office Web alojada aplicaciones, los clientes alojados y libre de aplicaciones de Office Web de Microsoft Software Assurance para clientes empresariales. Gratis, libre, gratis. Sólo pymes que opten por la Oficina 2010 aplicaciones web en lugar de comprar software de oficina regulares tendrán que pagar más, algunos en una estimación comparable (a Google Apps edición premier) $ 50 el precio. Puede que no sea $ 50, pero yo apuesto a que no es demasiado lejos.
Subscribe to:
Posts (Atom)